It’s the words you secretly dread to hear, “We’ve been hacked!”
Nobody wants to learn about a data leak at their company from colleagues. Or worse… reading about it first in the media. Unfortunately, such incidents have become commonplace.
A recent report by Risk Based Security tallied 3,932 publicly disclosed data leaks in 2020. From these breaches, the total number of records compromised topped 37.2 billion — a 141% spike from 2019.
Many of those records will end up for sale in the online criminal underworld.
Here you can find a booming trade for stolen account credentials and corporate secrets. Personally identifiable information (PII) also represents a prized commodity, exploited for fraud and identity theft.
Which begs the question: how do you know if any of your company’s data isn’t already for sale?
Or, how can you find out if your information is circulating the web? We’ll get to that in a second. But first, we need to understand how data leaks can impact your business and your customers.
What You Need to Know About Data Leaks
Data leaks can make a big dent in your company’s pocketbook.
Health insurer Anthem could have to pay over $100.0 million in fines following a recent breach.
Authorities penalized British Airways $229.0 million after the company fell foul of GDPR guidelines.
And regulators have issued stiff fines for other cyberattack victims, including Target, Marriott, and Desjardins Group.
Admittedly, I cherry-picked these high-profile examples to make my point. But even a small breach can have a large impact on a firm’s bottom line.
How much exactly?
Almost $3.9 million on average per incident, according to a 2020 study by IBM. That figure jumps to $8.2 million per incident for businesses headquartered in the United States.
IBM’s study included the obvious expenses of dealing with a data breach: detection and investigation, responding to the incident, notifying impacted customers, patching IT infrastructure, etc.
But their report also includes less obvious costs that follow such events.
For instance, think about customer churn that results from bad publicity. Sales prospects may also decide to go with a competitor.
In total, IBM estimates lost revenue accounts for as much as 40% of the cost of a data breach. Almost as much, in other words, as the explicit IT expenses usually accounted for by executives.
Additionally, data leaks can have an outsized impact on a firm’s stock price.
A study by Comparitech looked at 34 breaches between 2013 and 2016. Over the following year, researchers found shares of firms that have suffered a data breach trail broader market indices by 8.5%.
For an enterprise, that can represent billions of dollars in lost shareholder value. And a higher cost of capital can make it tough for companies to raise funds for new projects.
Ouch!
Average Cost Per Compromised Record by Type ($US)
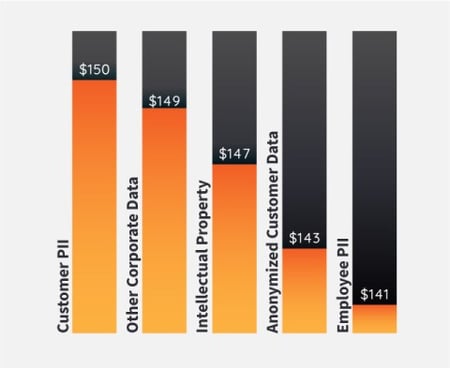 Source: IBM Security Cost of a Data Breach Report
Source: IBM Security Cost of a Data Breach Report
But it gets worse, as IDStrong security and information privacy consultant David Lukić explains.
“It takes compromised companies an average of 206 days to detect an attack and 73 days to contain it.”
“This means that your organization’s sensitive data could be vulnerable for almost seven months before you’re even aware.”
Obviously, the longer it takes for your company to detect a breach, the more it will impact your operations.
Delays give threat actors more time to harm customers and employees. And that could mean large, permanent damage to your organization’s reputation.
“Early detection is important because the longer an adversary remains on target, the deeper they can root themselves and the more time they have to collect information on the target.” explains Peter Morgan, President and Co-Founder of Phylum.
“Adversaries are most often motivated by financial gain, so the ability to harvest credentials or expose credit card information are the low-hanging fruit.”
“More complex operations may seek to steal intellectual property or use the target to launch further attacks against the target’s clients.”
And the longer it takes companies to spot a breach, the bigger the hit to the bottom line.
Long cycle breaches that take 200 or more days to detect are 37% more expensive on average than those detected quickly. And that figure rises for breaches in particularly sensitive industries, like finance, utilities, and healthcare.
How Data Leaks Put People At Risk
So, what can bad actors do with leaked data?
It depends.
Typically, hackers want to exploit this information for a quick buck. Others may have a political motivation.
For example:
Doxing: Doxing is the act of publishing a person’s private information without their consent. Bad actors might dox an individual for lots of reasons, such as harassment or shaming.
Financial Fraud: Stolen financial records fetch some of the highest prices on the dark web. And for good reason. Emptying out a victim’s bank account presents a quick way to cash in on leaked data.
Extortion: Leaks can include sensitive data such as photos, videos, health records, and chat logs. In other words, information victims would rather not have exposed to the whole world. That can make them targets for extortion.
Identity Theft: Leaked PII makes it easier for criminals to assume a victim’s identity. Thieves can then buy drugs, take out a loan, or apply for a credit card in someone else’s name. This can have dire consequences for victims. Identity theft can make it difficult to get a job, receive tax credits, or open a bank account. And it can take years for victims to clear their names.
Credential Stuffing: Security experts always warn against reusing the same password across multiple sites. Unfortunately, most people don’t follow that advice. So one leaked password often allows hackers to access many accounts owned by a victim.
Social Engineering: Attackers can use seemingly harmless PII, like names, addresses, and phone numbers, to access other data. For example, a criminal could contact an agency under the guise of a victim. Then they would use leaked information to pass any security screening questions. Once through, attackers can request account changes or access secured facilities. That could present a serious physical security risk for organizations.
Spear Phishing: Spear phishing is a term used to describe highly targeted phishing emails sent to well-researched victims. Data leaks give threat actors information to craft more convincing messages.
The Warning Signs You’ve Been Hacked
So how can you protect your customers by spotting data leaks faster?
And how can you find out if your company’s data is already for sale online?
Internal feeds often represent the first sign of a breach. Any unusual network traffic patterns could signal an intrusion.
“Maybe the internet feels slow. Maybe a computer or other device behaves strangely. Or maybe systems inside your network decide to interact with Russia, China, Iran, North Korea, or other hostile location.” explains author and cybersecurity professional Greg Scott.
“Or, for retailers, maybe POS (point of sale) systems are moving traffic to/from somewhere new.”
“Unusual network traffic patterns are the hardest to detect because very few organizations monitor network traffic, and so very few know what normal looks like.”
Furthermore, you can also spot data breaches in fringe online communities. Here threat actors sell, share, and discuss leaked data.
For example:
Paste Sites: Paste sites are content hosts that allow users to share plain text files. Pastebin ranks as the largest. But you can find dozens of others like Pastie.org, LeakedIn, SkipPaste, and DeepPaste. Programmers love using these services to share code snippets. But bad actors also exploit paste sites to publish and advertise data leaks.
Chan Boards: Chan boards are anonymous online forums. Admittedly, they have a bad reputation. But most of the content discussed on these sites is harmless. Though on occasion, members have used these services to leak stolen data.
Criminal Forums: Deep and dark web forums serve as hubs for criminal activity. After a breach, hackers can sell stolen data in these underground marketplaces. Ads often resemble a posting you’d see on eBay or Craiglists. Thieves will explicitly name the hacked company. And in the description, they will sometimes include a sample of breached data.
Free Services: Several free sites compile data from thousands of confirmed breaches. The largest include BreachAlarm, DeHashed, and Have I Been Pwned?. If your email was compromised in a notable breach, these services will let you know.
The Bottom Line on Data Leaks
Each year, companies have to fend off more attacks from adversaries. Some of these attacks will be successful.
Building better walls around your IT system is no longer enough. Teams need to watch both internal and external sources for signs that a data leak has taken place.
That can go a long way to minimizing the financial fallout from such incidents.
And more importantly, better protect your employees, customers, and executives.
