The best way to protect your people, assets, brand, and data is to know what’s coming. Our threat intelligence OSINT platform, Navigator, is designed to help you do exactly that.
Navigator utilizes OSINT tools to provide a comprehensive and curated overview of active physical threats, information leaks, security exposures, and risks to your assets, operations, and people, all in one integrated OSINT platform.
Navigator ensures early risk detection, giving you a distinct advantage. Early detection allows security teams to stay ahead of issues that can disrupt your business or brand, damage property, or put your people at risk. The real-time detection and validation process identifies risks based on the current online environment and takes quick action to reduce them. Navigator does this through methods such as automation and filtering posts through keywords.

Collect & Aggregate Threat Actors
We pinpoint vulnerabilities and potential threat actors 24/7 through automated collection using our OSINT platform. These risks are virtually impossible to identify without the help of dedicated automated collection technology. Navigator does this hard work by collecting data from all public online sources, including:
- Social Media
- Blogs, Boards, Forums
- Alternative Social Channels
- Classifieds, Paste sites
- Deep Web sites
- Dark Web sources
Once Navigator detects a threat, it alerts your team and provides multiple tools for validation, identity resolution, and dissemination.
Understand the breadth of your organization’s threat landscape
Threats to business continuity are a constant concern for every organization, and larger organizations tend to have more live threats to address.
Our deep intel-driven, threat intelligence service platform provides a broad, legible view of your organization’s threat landscape using several tools:
- Custom Keyword Tracking
- Boolean Search Terms
- Curated Threat Feeds
- Geo-location
- Inferred Location
- Analyst Annotated Events

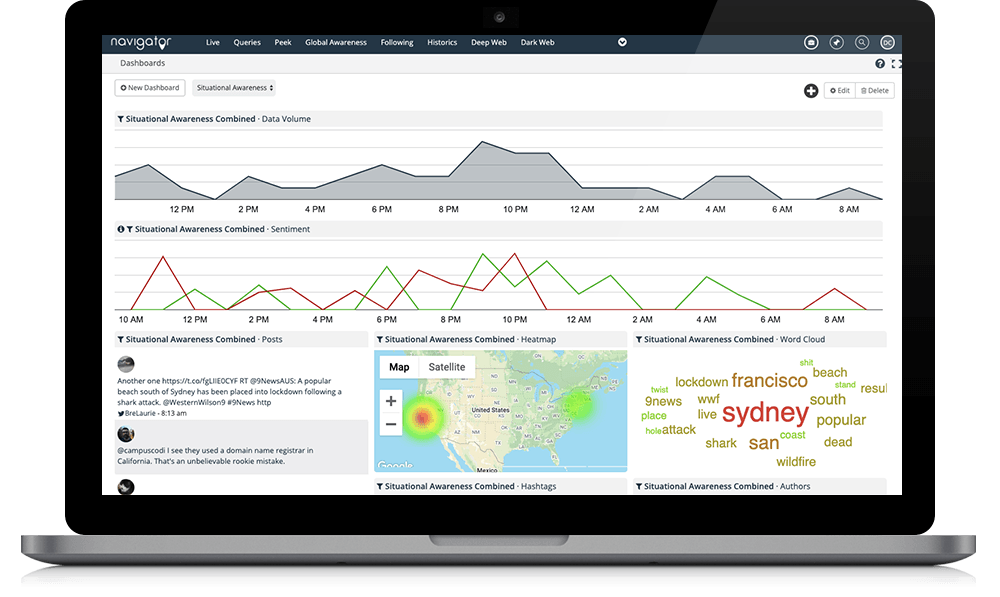
Intelligence at Your Fingertips
Powered by data, our OSINT platform's tools analyze and immediately validate your intelligence with our suite of investigative tools, including:
- Global Identity Resolution
- Targeted Monitoring
- Threat Intel Management
- Public Records on US Individuals
- Dashboards/Visualization
- Sentiment Analysis
- Threat Connectivity
Stay Notified Around the Clock
You will never have to worry about missing any threat with our array of real-time alerts and notifications through SMS, email, mobile app, and Slack. We will ensure that your team is kept up to speed on all risks as they arise and develop.

Feature Highlights
Global Awareness
Display company assets on the map and alert your team of potential threats within a custom radius, including extreme weather, disruptive events, public safety, etc.
Live Monitoring
Gather and filter data from millions of online sources with custom parameters, reducing the noise to return only the most relevant posts and intelligence.
Identity Resolution
Rapidly identify and validate potential risks by analyzing a user's global digital footprint, and delve into detailed information on individuals in the US with our Public Records offering, to enhance verification speed and streamline operations.
Threat Management
Simplify your investigations by consolidating intelligence discovery, validation, and ongoing management of threat actors, specific events, or business entities.
Executive Protection
As a corporate security analyst, you are responsible for identifying and mitigating threats to your company's executives. With the rise of online threats and social media's ubiquity, it is more important than ever to have access to intelligence about potential risks. If you are prepared, you can respond and react immediately.
Workforce Protection (travel safety)
As a corporate security professional responsible for workforce protection, ensuring the safety of your employees while traveling is a top priority. With an increasing number of travel-related incidents and emergencies around the world, it is more important than ever to have access to timely intelligence and threat management tools.
Learn more about how our OSINT Platform can help with Protective Intelligence.
Geo-political Risk Management
As a corporate security analyst, your organization faces a range of potential geopolitical risks that can impact your operations, employees, and assets. From political unrest to economic instability and natural disasters, there are many factors to consider when monitoring for and managing these threats.
Physical Asset Protection
As a security professional responsible for physical asset protection, ensuring the safety of your organization's assets is a top priority. With a wide range of potential threats, you need the latest information to successfully monitor threats to your physical infrastructure, offices and critical locations.
Event Security
As a corporate security professional responsible for event security, you understand the importance of staying ahead of potential threats and ensuring the safety of attendees, staff, and assets. With an increasing number of potential threats, including extremism, weather events and violence, it is more important than ever to have access to timely intelligence and threat management tools.
Event Detection
As a corporate security professional responsible for detecting disruptive events, you need to be able to detect potential events that pose a threat to your business operations before they escalate. This is important so you can ensure you take proactive measures to mitigate risk.
Learn more about how our OSINT Platform can help with Location & Event-based Threat Monitoring
Brand Protection
As a corporate security analyst, monitoring threats towards your brand is critical to maintaining the reputation and trust of your customers. In today's fast-paced digital landscape, threats to your brand can emerge at any time, from anywhere in the world.
Anti Piracy
As a professional in charge of protecting digital content, digital piracy is a major concern. Digital piracy can result in lost revenue, damage to brand reputation, and even legal consequences. In order to protect your company from digital piracy, you need a comprehensive anti piracy solution that can help you detect and monitor potential threats, enabling users to respond with the utmost urgency.
Content Protection
As a professional in charge of content protection, your intellectual property is critical to your business success. Unauthorized access to your content can result in lost revenue, damage to your brand reputation, and even legal consequences.
Learn more about how our OSINT Platform can help with Digital Risk Protection
As a corporate security analyst, finding and understanding the individuals and groups that pose a threat is critical to protecting your organization. Threat actors are constantly evolving their tactics and strategies, making it difficult for companies to have the context they need to reduce potential risks.
Learn more about how our OSINT Platform can help with Threat Actor InvestigationsLEARN MORE
Book a Discovery Call
Our team of experts are here to set you up with your customized security solution.
Get Started