LifeRaft + Topo + Chubb
2020 was a banner year for all-hazard threats. Organizations relied heavily on security teams to keep their colleagues and offices safe from weather disasters, civil unrest, a worldwide health crisis, and degrading economic conditions.
In January, we joined the Global Security team at Chubb and Topo.ai to have a conversation about mitigating operational disruption — and below are the top 10 takeaways from the webinar.
1. Know the difference between intel you can glean from different parts of the internet. Here are some examples:
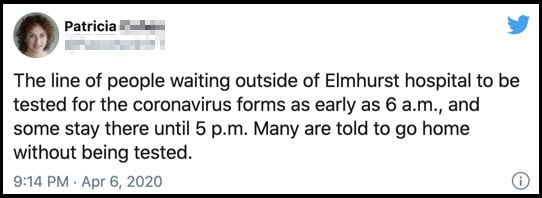
Social media: understanding links between accounts/communities, patterns of behaviour, social footprint/ digital profile insights
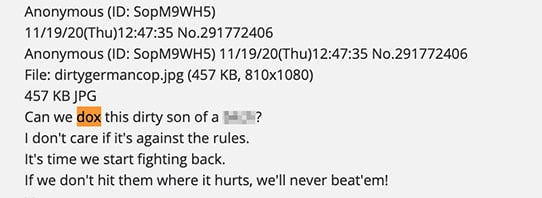
Deep web: like-minded individuals planning threatening events or data dumps for doxxing
Dark web: often transactional — buying and selling data or sometimes illegal products/services
2. Social media is most effective when proactively monitoring for breaking events, intel gathering, and to get a detailed understanding of a specific location or topic. However, it is not the best source for global events with lots of online chatter. Instead, turn to deep web sources and targeted Boolean logic.
3. Start with the end in mind — that is, identify what types of data are critical to know to make decisions or share key stakeholders. Once you’ve determined those specific needs, include those terms in advanced searches using and/or operators for finding the needle in the haystack.
4. Consider which high-risk issues warrant immediate notification for certain people/teams (for real-time alerts) and which topics, such as ongoing/evolving issues, are better suited for rollup summaries (passive awareness). This will help reduce alert fatigue but keep communication open and available for evolving situations.
5. When facing any complex or long-term crisis, identify the risk metrics that matter most to your organization. These should be based on your business, profitability drivers, culture, and tolerance for risk. If these are coming from many sources and need to be correlated, you will either need a lot of time to conduct the analysis or the right technology to analyze the data for you.
6. When you’ve determined the metrics that matter the most, use that data to establish risk thresholds and make decisions based on that data. ‘Database decision making’ helps reduce the role of personal opinions and instead focuses on a particular set of benchmarks that can be adjusted if needed. Should there be negative impacts from a given crisis, a set of benchmarks approved by leadership also provides a more defensible rationale than personal opinions.
7. What about Duty of Care when the workforce is increasingly remote: it’s evolving as we speak. There are security standards for the workplace that simply cannot be applied to a Work From Home environment. Focus on communications directly with the employees — a good place to start is using surveys to understand employee needs and impact. This will help inform how and where security can be involved to protect against threats in a virtual or remote scenario.
8. Work with HR, legal, communications, and other stakeholders to understand what data is best for mitigating risk and how to share relevant information between teams. From there, keep employees as informed as possible on how protocols are being developed and rolled out. Take into account which information should be as immediate alerts vs. rollup summaries.
9. In 2020 security and GSOCs in particular became the powerhouse of data and intelligence to support difficult decision making. Security earned a seat at the table with executive leadership. This in turn created a much larger demand on the time of security professionals as pre-existing risks and security operations continued to be a priority. In many organizations, this has created the risk of burnout. Remain vigilant about burnout by knowing your security team’s limitations and being empathetic to the challenges they may face at home. You don’t want to lose good people to burnout. Leverage the partnerships you’ve formed during the pandemic.
10. With this increase of responsibility and need for data-backed decisions, teams should leverage data and new technology. As an example, provide insight of how many sources you’re monitoring, topics/issues you’re tracking, how many alerts are being processed, incidents you are vetting, investigations you are conducting.
BONUS:
Lean into the technology partners you are working with — a sign of a good vendor is being able to call them up, tell them what you’re dealing with, and relying on them to rise to the challenge when the world around us is rapidly changing.
