As a physical security pro, you have a lot on your plate.
Teams must defend a growing number of assets: worksites, employees, infrastructure, intellectual property. And as companies expand internationally, they have to stay up to date on events around the world. Yet given a shortage of qualified analysts, no one has time to comb through the stacks of data.
What’s worse? Threat actors keep coming up with new ways to attack your organization.
They share tactics to defraud businesses. They collect information on employees to launch phishing campaigns. They probe for weak points in your infrastructure to breach defenses.
By the time an incident takes place, it’s often too late to react. And that can come with a big price tag, through fines, damage, and business disruptions, for your company.
Jump to: SECTION 1: Threat Intelligence 101 | SECTION 2: The Nuts and Bolts of Threat Intelligence
SECTION 3: Applications of Threat Intelligence | SECTION 4: Scaling Your Threat Intelligence Program
So what’s the answer?
Savvy businesses have seen the value of threat intelligence for physical security. This means keeping up on the goals and tactics of bad actors before an incident occurs. And it also means considering risks ignored by most security teams, such as geopolitics and brand protection.
This can pay off for your organization in many ways.
Security teams, for starters, can reduce alert fatigue and make smarter decisions.
It better ensures the safety of employees, property, and customers.
And it allows security leaders to quantify risk, making it easier to justify buy-in from executives and board members.
Of course, incorporating threat intelligence into your security program can be daunting. And some may be unsure where to get started.
That’s why we wrote this guide.
In this report, we’ll explore exactly what is threat intelligence. You also learn techniques to beef up your physical security defenses. And finally, you’ll see how you can build and scale a threat intelligence program for physical security. Let’s dive in.
SECTION 1: Threat Intelligence 101

What is Threat Intelligence?
Threat intelligence refers to any information organizations use to better understand their adversaries.
It provides context for companies to make better decisions about their physical security. And as a result, teams can better forecast and respond to incidents that occur.
In this sense, threat intelligence to companies is like a preflight weather report to a pilot.
In aviation, like a corporate setting, plotting a course into a storm could have dire results. We expect pilots to set the safest, optimal route after weighing their risks and options.
Threat intelligence plays the same role in organizations.
It’s no longer enough to be the “guard at the gate” waiting to stop bad actors. Security teams must instead predict, prevent, and prepare for attacks before they occur. But companies can only achieve those goals with the right tools and information on hand.
So why has this topic become more important in recent years?
Several reasons explain why threat intelligence has become so relevant for physical security:
Risks have become more complex. Digital spaces now impact the physical world and vice versa. Companies also face more complex risks than ever, like terrorism and organized crime. So you have to watch more spaces, both on and offline, to understand the threats to your organization.
Business has gone global. Practices, such as offshoring and foreign expansion, force companies to manage at a distance. Remote employees also mean a spread-out workforce. You’re no longer watching a handful of worksites in one city or one country. You might have to track hundreds or thousands of facilities worldwide.
A global skills shortage. More threats means increasing demand for trained security professionals. But these are often stressful jobs with heavy workloads. And that results in large amounts of burnout and turnover. For that reason, businesses need threat intelligence technology to automate data collection. They also need more relevant intelligence on hand to make informed decisions.
To be clear, we’re not only talking about protecting a business from digital risks.
Oftentimes, threat intelligence gets lumped into the realm of cybersecurity. It’s usually mentioned in the context of defending network systems. Not true.
In reality, threat intelligence provides value for any security professional, digital or otherwise. And it’s as important for mitigating real-world, physical threats such as theft or violence.
Likewise, some people use words like data, information, and threat intelligence interchangeably. But these represent completely different concepts.
Data consists of individual facts about an entity or an event. For example, think of network traffic logs or key fob entry records to a room.
Meanwhile, analysts glean information by combining data points to answer a specific question.
How many users have logged onto a network? How many people have entered this facility?
But threat intelligence gives context.
It weaves large amounts of data and information together. And in this process, analysts can better understand a threat.
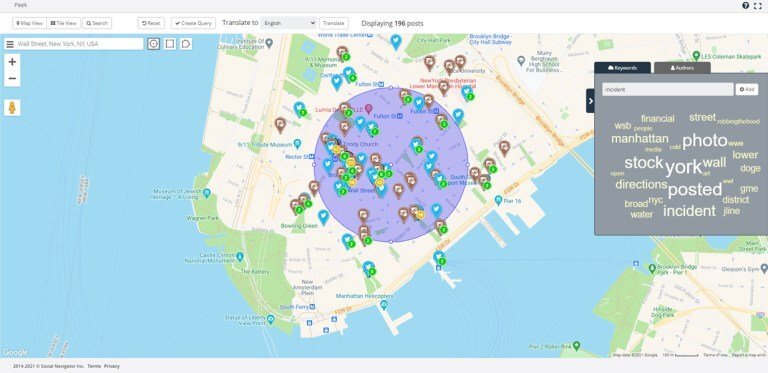
In other words, threat intelligence doesn’t just explain the who, what, where, and when something is happening. It can also outline why an event has taken place. This added context is critical. As it’s the key ingredient that allows those in charge to make better decisions.
How is Threat Intelligence Used for Physical Security?
Threat intelligence has a number of applications for physical security.
Of course, it’s most immediate value comes from preventing incidents altogether. But the practice also allows you to assess risks, reduce alert fatigue, and spot vulnerabilities in your operations.
Here’s a broad overview of how companies might apply threat intelligence for physical security:
Executive Protection: Executives represent one of your company’s biggest assets. That also makes them a big target. Managers face threats from criminals, disgruntled customers, and resentful employees. And possible risks include everything from fraud and doxxings to violent attacks. An intelligence led security program allows your team to be alerted to and address these threats, providing your VIP with better protection.
Crisis Response: The unexpected happens. And like Mike Tyson once said, everyone has a plan until they get punched in the face. A well developed threat intelligence program, however, allows security teams to better understand the nature of emergency when it happens. And better decisions in the heat of the moment will ultimately ensure the safety of personnel. Not to mention mitigating the cost of any business disruptions.
Brand Protection: Fraudulent uses of your company’s image can harm your sales, brand value, and customer relationships. For instance, criminals may set up fake websites that imitate your homepage. This could trick customers into revealing personal information. Alternatively, counterfeiters may attempt to pawn off fake products on an online bulletin board. In both cases, illegal usage of your brand can harm customers. And in the long run, this could permanently damage the public’s perception of your company.
Insider Threats: Often the biggest threats to your company come from inside the organization itself. This could be the result of negligence. For example, an employee accidentally posts a picture of their work ID badge to social media. Alternatively, insiders could have more malicious intentions. In both cases, intelligence allows your team to quickly detect and investigate potential threats
Fraud Prevention: Threat intelligence collected from criminal groups provides a window into their motivations, tactics, and techniques. This can help organizations stop anything from shoplifting and payment fraud to money laundering and credit card theft.
Active Threats: Some companies have to deal with individuals bringing a weapon to the workplace. In the worst case scenario, these bad actors could turn that weapon against employees, managers, or customers. To address this risk, security teams can monitor the web for shooter manifestos or other indicators of a threat.
Data Breaches: Data breaches can damage confidence in your organization. Leaked personal information also exposes employees and customers to a variety of risks like fraud, doxxings, and phishing attacks. Threat intelligence software allows your team to detect data leaks across criminal forums and dark web markets. By cutting the response time between a leak and its detection, you can significantly reduce the fallout from such events.
Misinformation: Technology, such as Photoshop, deep fakes, and doctored audio, make it easy for malicious actors to spread misinformation. Social media only makes this process easier. Yet even these rumors are false, misinformation can still have real consequences for your operations. But by detecting such issues early, companies can better address such challenges.
Monitor Infrastructure: Companies may have hundreds or thousands of assets around the world. It might not be feasible to hire guards to safeguard all of these properties. But a well developed threat intelligence program can allow teams to spot incidents of theft, vandalism, or trespassing as it emerges online.
Third Party Risk: Starting relationships with new partners comes with a swath of risks. You can keep your company safe by conducting your due diligence beforehand. By spotting potential problems ahead of time, your organization could sidestep potentially expensive incidents.
Who Benefits From Threat Intelligence?
Some people perceive threat intelligence as simply a research service for specialized analysts. But the practice goes far beyond that.
In reality, threat intelligence for physical security has a number of benefits for analysts and leaders in your department.
For instance:
Security analysts. Front-line personnel have to shift through a deluge of data. Threat intelligence gives these teams tools to prioritize alerts, minimize false positives, and respond faster to incidents. That means better decisions in the heat of the moment.
Security leaders. Security leaders can use intelligence to better assess business requirements and develop mitigation strategies. Threat intelligence can also be exploited to quantify risks in monetary terms. That represents valuable information when justifying security investments to executives and board members.
Other stakeholders. Threat intelligence can benefit stakeholders outside the global security operations center, including brand protection, risk management, and fraud prevention teams.
Ultimately, the benefits of threat intelligence go right to the bottom line.
You can track some cost savings quite easily. Mitigating and responding faster to iccidents means fewer fines from regulators, reduced business downtime, and smaller losses in the way of theft or fraud. Other savings can be much harder to measure, but no less tangible.
Take a robbery at a retail outlet, for instance. These events can lead to higher employee turnover at nearby locations. That costs companies considerably in the way of recruitment and training new workers.
Alternatively, consider the sale of counterfeit products.
Customers might not realize they bought a knock-off from criminals. But if the product malfunctions or wears out too quickly, your company’s reputation will still get tarnished.
In both cases, it might be tough to assign a specific dollar value to incidents. But regardless, investments in a threat intelligence program can have a large return.
Read More:
What is Threat Intelligence (and Why Does It Matter for Physical Security)?
-
SECTION 2: The Nuts and Bolts of Threat Intelligence

The 6 Steps of a Successful Threat Intelligence Program
The “intelligence cycle” is the process used to turn data into useful information. And it represents the core of any surveillance program.
It doesn’t matter whether you want to protect an executive or stop an active threat. The cycle involves the same six steps:
| Planning : Outline the high-level needs of your intelligence program. What are your goals? What assets need protection? What threats does your company face? How should you address those threats? This will set the tone for every step to follow. | Collection: Gather raw data from lots of threat feeds. Specific sources will vary, of course. Common examples include social media, news outlets, and network logs. But the more feeds the better. Wider coverage means you’re less likely to overlook a threat. |
| Processing: Raw data is rarely useful on its own. You must first parse, index, and normalize inputs. This removes false positives and duplicated data points. It also makes it easy for analysts to interpret. | Analysis: Analysts study the processed data. Afterward, they turn this information into actionable intelligence for decision-makers. |
| Distribution: Analysts send out their commentary to those who need it. This could be in many formats, such as reports, videos, presentations, or blog posts. | Feedback: Teams should consider feedback from stakeholders with each cycle. What went right? What went wrong? Are there new threats to look out for? This ensures your process can adjust to changing conditions. |
Of course, this cycle is only a rough guide. In the real world, different stages can occur at the same time. Decisions can also get made before an organization has completed a formal cycle.
Still, these six steps serve as a useful model to picture how raw data gets turned into intelligence.
The Types of Threat Intelligence
Analysts use “threat intelligence” as a broad umbrella term. But you can break the topic down further into two main categories: tactical and strategic.
This distinction is important.
Different members of a team have their own needs and knowledge. The goals of your Chief Security Officer look a lot different than that of an analyst. So they also need different types of intelligence.
Tactical intelligence helps security teams detect attacks and understand emerging threats.
It provides specifics on the tactics, techniques, and procedures of bad actors. It’s also used to improve existing physical security controls and incident response.
Typically, these reports go to those involved in the daily defense of an organization. Think of guards, analysts, and managers.
These people usually have a lot of technical knowledge. So reports often dive deep into the nitty-gritty of security operations.
For this reason, you might also hear these reports referred to as technical or operational intelligence.
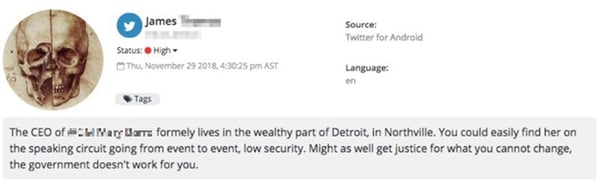 A threatening post directed towards a senior executive, discovered by Navigator.
A threatening post directed towards a senior executive, discovered by Navigator.
Strategic intelligence, in contrast, gives a “bird’s eye view” of the threat landscape.
As you would expect, analysts create these reports for high-level executives. The goal is to help those in charge understand the impact of their decisions. And they might gloss over specific incidents or technical details.
Instead, strategic intelligence provides an overview of threats in a particular domain.
What are the potential risks? What assets do we need to protect? What types of bad actors should we look out for?
These reports usually go beyond daily operations. And analysts may have to connect security objectives to related fields like economics and geopolitics. These topics get woven together to provide the full picture.
Threat Intelligence Sources
Threats can come from a lot of places. A disgruntled customer could make violent threats against an executive in a forum. A careless employee might post their ID badge on a social network.Shoplifters may offload stolen products through eBay.
That’s why “data diversity” has become an important topic in the security operations center. It’s sort of intuitive.
You can’t, after all, respond to a threat if you don’t see it. So by taking in as much data as possible, you’re less likely to overlook a serious risk.
Unfortunately, the number of places threats can hide, especially online, keeps growing.
The big social media sites have clamped down on hateful and violent users. So radical content producers, and the people that follow them, have moved to new alt-tech websites. We’ve seen a similar trend in the criminal underworld.
Authorities keep shutting down popular darknet marketplaces. In response, thieves and hackers have regrouped on more obscure sites.
That means not only does the number of potential threat actors keep growing. So too does the number of places where they can talk and organize.
And that makes it tougher for security teams to spot bad actors before they strike.
The solution, of course, is to cast a wide net and take in as much data as possible. Here’re some examples:
Internal Feeds: Examples include network logs, video surveillance, and access control records. These sources often provide the most relevant information. After all, they often come directly from the assets your company wants to defend.
Marketplaces: Criminals can exploit online classifieds and marketplaces to sell stolen products.
Media: News outlets, such as Fox, CNN, and Bloomberg, produce timely reports on current events. Teams can boost their coverage by subscribing to first alert and research services.
Social Media: Social channels, like Reddit, Twitter, and Parler, offer vast amounts of useful data. Events often appear on these networks first, sometimes hours ahead of new outlets. Teams can also glean on-the-ground insights from posts and images uploaded by users.
Industry Experts: Security blogs, websites, and vendors represent knowledgeable sources of information. These sites cater specifically to security teams. For that reason, their coverage tends to focus on more relevant threats to businesses than what’s discussed on mainstream news outlets.
Paste Sites: Paste sites allow users to share plain text files. Much of the content on these forums is rather benign. Criminals, however, use paste sites to market illegal products and services. Bad actors also exploit them for doxings and data leaks.
Chan Boards: Chan boards are anonymous forums based around sharing images alongside text and discussion. The largest include 2chan and 4chan. While these sites have a bad reputation, most content here is harmless. Though on occasion, bad actors exploit chan boards for doxings, harassment, and data leaks.
Darknet: The darknet refers to encrypted online content not indexed by regular search engines. This corner of the web serves as a haven for criminals and extremists. While tough to access, it serves as a great source of threat intelligence.
At LifeRaft, we track a wide range of data feeds. This includes public records and social media all the way down to the deepest corners of the dark web.
Such breadth means customers are less likely to miss a serious threat. It also makes it easier to investigate a threat once spotted.
But it’s not enough to watch a whole bunch of feeds.
The internet keeps changing. And where threat actors lurk today might not be where they’re hiding tomorrow.
That’s why security teams must always stay on the lookout for new, relevant data feeds as they pop-up.
“The threat landscape the internet created, and social networks have popularized is an ever-expanding galaxy. Monitoring for online threats and risk indicators has proven to prevent potential disasters and save lives, so we need to cast our net far & wide while outputting data that can be efficiently utilized. Platforms will continue to be built that provide anonymity and protection from censorship, but will act as a playground for potential threat actors and cyber criminals. It’s important not to let these emerging dark areas become blind spots.”
— Kyle Baker, OSINT Analyst LifeRaft Inc.
Take Parler, for instance. At LifeRaft, we first started covering the social network in summer 2020. Over the following months, the site grew substantially thanks to a hands-off approach to content moderation.
But that lax policy eventually backfired. In January 2021, some users exploited the network to organize riots at the U.S. Capitol building.
Incredibly, however, the event blindsided many in the intelligence community.
Much of the riot planning happened right out in the open through public posts. But because few analysts checked or even knew about Parler, they missed this threat completely. Incidents like this happen all the time online.
That’s why it’s important to not only watch a large number of data feeds. You also need to review and update your sources on a regular basis.
Read More:
What is the Dark Web?
What is the Deep Web? A Quick Guide for Beginners
5 Alt-Tech Social Networks You Need to Know
What is Reddit & Why is it Valuable for Threat Intelligence?
-
SECTION 3:
Applications of Threat Intelligence

Workplace Violence
How safe is your organization from workplace violence?
Most security teams find themselves stretched for time and resources. Analysts often only have enough cycles to triage the most serious threats — usually those impacting the C-suite.
So what happens to lower-level incidents in the workplace? More often than not, they fall to the bottom of the priority list. But this can represent a huge oversight.
A failure to address workplace violence puts the safety of staff and customers at risk. It can also impact the bottom line through business downtime, reputational damage, and employee turnover.
Worksite assaults alone cost businesses in the United States more than $121.0 billion annually. Moreover, out-of-court settlements resulting from violence now top an average of $500,000 per incident.
As a result, more security teams have started to ask: How can we make our workplace tougher targets to attack? And if an incident takes place, how can we respond more effectively?
One possible answer? Proactively watching the web for relevant threat intelligence.
Admittedly, web monitoring isn’t the panacea some of its proponents claim. Not every threat actor publishes their plans online. And depending entirely on this tactic could give a false sense of security.
That said, teams have found success with this technique when applied as part of a holistic system. It should be seen as just one more tool in their arsenal. Another addition to your collection of different strategies and techniques. And in this context, it can serve as a real force multiplier for addressing workplace violence.
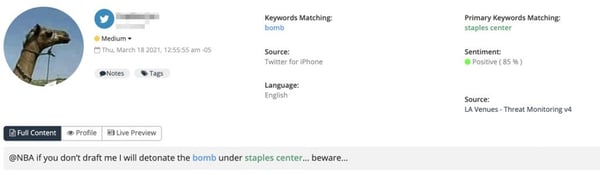 A potential threat posted to social media, discovered by Navigator.
A potential threat posted to social media, discovered by Navigator.
In a shocking 2019 example, authorities arrested a 26-year-old man plotting a mass shooting at a Florida Wal-Mart.
Law enforcement discovered the threat after this individual posted a message to Facebook that read, “3 more days of probation left then I get my AR-15 back. Don’t go to Walmart next week.”
Over the following weeks, law enforcement uncovered similar plots nearby in Daytona Beach and Tampa Bay.
In Ohio, police uncovered another plot after a man threatened a local community center on Instagram.
The FBI raided his home soon after. Inside, they discovered a large weapons cache, in addition to body armor and anti-Semitic propaganda.
So what type of threats should teams be on the lookout for?
Incidents of workplace violence fall into one of four buckets:
- Criminal Intent. Attackers have no legitimate relationship to the business or its staff members. Examples of crimes that fall into this category include robberies, shoplifting, or trespassing. Terrorist attacks and other ideological violence would also fall into this group.
- Customer/Client. Attackers have a legitimate relationship with the business. For example, think of customers, patients, clients, or students. And incidents occur during a staff member’s normal work duties. Employees in retail and healthcare represent the most common targets of this type of violence.
- Worker on Worker. Occurs when an employee or ex-staff member attacks others at a worksite. These incidents are often sparked by interpersonal conflicts, work-related disputes, or financial losses. Furthermore, supervisors and managers rank as the most common targets of violence in this category.
- Personal Relationship. The attacker has a relationship with the target. The most common example of incidents in this category would be victims of domestic violence. Women represent the most frequent targets of these attacks. And the risk of an incident increases when one party attempts to leave a relationship.
In all of these situations, it’s important to cast a wide net for information.
Bad actors, especially criminals, have migrated to murkier corners of the web such as the darknet. For that reason, you need to look beyond mainstream sites. Furthermore, be sure to keep screenshots of any relevant intelligence.
Moderators may remove posts. Users could delete content. Or accounts could disappear entirely.
That can compromise your investigation. And down the road, losing evidence can make it harder to enlist the help of law enforcement.
Finally, cover your tracks.
If a target learns they’re under surveillance, they might remove posts or move to another forum. That’s why it’s smart to use a VPN or other privacy software to mask your online activities.
Collecting such threat intelligence won’t prevent all incidents of workplace violence. But it can go a long way towards ensuring the safety of your staff and customers.
Read More:
Workplace Violence: How to Spot and Address It At Your Company
-
Data Breaches
Each year, companies fend off more cyberattacks. And thanks to sheer volume, more and more of these attacks will be successful.
A recent report by Risk Based Security puts the problem in context.
For 2020, the consultancy tallied 3,932 publicly disclosed data leaks.
In those breaches, the number of records compromised surpassed 37.2 billion. That’s more than double the number reported a year prior.
And these events can make a big dent in a company’s bottom line.
On average, a data breach cost businesses almost $3.9 million per incident. And that number jumps to $8.2 million per incident for companies based in the United States.
More alarmingly, it takes businesses on average 206 days to detect a breach. And then another 73 days to contain it.
Such a slow response gives attackers more time to do damage. And ultimately, that will mean a bigger hit to your company’s reputation and the bottom line.
“Early detection matters because it enables organizations to respond to a security incident sooner and allows the responders to implement controls. This can prevent the incident from spreading to other areas of the network, effectively minimizing potential damages.”
— Matt Campagnola, Infosec Cybercrime Educator
The takeaway here for security teams is that building better walls around your I.T. systems is not enough.
Some attackers will inevitably slip through your defenses. Instead, companies need to watch both internal and external sources for signs that a data leak has taken place.
That can go a long way to containing the damage from such incidents. And more importantly, better protect your employees, customers, and executives.
So where should you be looking to spot data leaks?
“Areas of the network and assets that are highly sought after by adversaries are typically the best places to look for early breach indicators.” explains Infosec cybercrime educator Matt Campagnola.
“These can include the edge of an internal corporate network where it connects to the wider internet, privileged accounts (e.g., an administrator or executive account), critical network devices such as a domain controller, or around databases containing sensitive information.”
Moreover, you can also spot data breaches in fringe online communities. Here, threat actors sell, share, and discuss leaked data.
Here’re a couple of methods to accomplish this:
Free Services: Numerous free sites compile data from confirmed breaches. The largest include BreachAlarm, DeHashed, and Have I Been Pwned?. If your email was compromised in a notable breach, these services will let you know.
Deep Web Forums: Security teams should keep tabs on deep web platforms like Chan boards, paste sites, and social networks. The vast majority of content shared on these services is harmless. But on occasion, attackers have exploited them to leak or sell stolen data.
Dark Web: Dark web forums serve as hubs for criminal activity. After a breach, hackers can sell stolen data in these marketplaces. Postings resemble ads you’d see on Facebook and Craiglists. Thieves will often name the hacked company along with a sample of breached data.
Detecting a breach quickly can mitigate the financial fallout for your business.
As mentioned in the IBM study above, breaches can cost companies millions per incident. But figures vary widely.
Longer cycle breaches (those that took more than 200 days to detect) cost 37% more than incidents detected sooner. And that number rises for particularly sensitive industries like finance, utilities, and healthcare.
Average Cost Per Compromised Record by Type ($US)
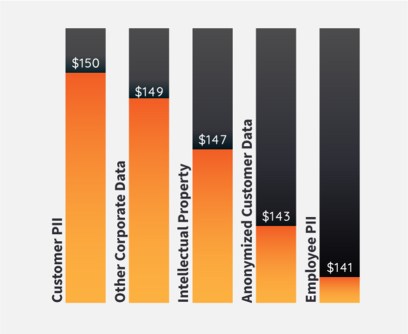 Source: IBM Security Cost of a Data Breach Report
Source: IBM Security Cost of a Data Breach Report
Furthermore, IBM broke down their results by businesses that invested in threat intelligence software versus businesses that didn’t use automated tools. Researchers found breaches in the former group cost 36% less than the latter.
In other words, security automation tools are a bit like taking out a home insurance policy on your house.
You hope you never need to make a claim. But the small cost upfront can payoff big in the event something goes wrong.
Read More:
Data Leaks: Is Your Company’s Data Already For Sale Online?
-
Insider Threats
When most people imagine a threat actor, they tend to picture outsiders. Shoplifters. Hackers. Gunmen. Terrorist. Rioters. Organized crime.
But what if the real threat lurks inside your company?
Last year, reports surfaced of a Russian national offering bribes to Tesla employees. In exchange, he instructed them to install ransomware on the company’s network.
Near the same time, Twitter revealed two ex-employees stole data illegally on behalf of the Saudi Arabian government.
More recently, authorities have uncovered insider-led scams at Shopify, Yandex, and Ubiquiti Networks.
In fairness, I cherry-picked these examples for shock value.
But a growing number of reports show insider-led attacks are on the rise. And they pose an outsized risk to the safety of your employees and customers.
But exactly what are insider threats? And how can you detect them?
Simply put, insider threats are people that use their access to corporate assets to hurt the business.
Employees represent the most common type. But these actors could also be partners, contractors, or ex-workers.
Gartner Security breaks insider threats down into four categories.
- Goofs: Goofs, otherwise know as accidental insider threats, are individuals that accidentally jeopardize the security of a business. An incident might result from a mistake. Or it could result from sneaking around security measures for the sake of convenience. But Goofs usually don’t have malicious intentions.
- Pawns: Pawns represent unwitting insiders tricked by attackers into performing malicious actions. Attackers usually manipulate pawns through social engineering tactics like spear phishing or baiting.
- Collaborators: Collaborators work with a third party to conduct attacks. These third parties could include criminals, competitors, or even countries. And they may have several motives, such as fraud or IP theft.
- Lone Wolves: Lone wolves are malicious individuals that operate on their own. They present an especially large risk when placed in a privileged role, like a system admin. And because they don’t communicate with outsiders, they’re often tough to detect.
Unfortunately, insider threats represent a bit of a blind spot for protection teams.
It’s easy to imagine outside actors inflicting damage upon our organizations. It’s harder to picture Bob in accounting as a serious threat. But that would be a mistake.
Insiders are well placed to commit fraud, steal inventory, or damage equipment. Rogues can also leak data or intellectual property.
Research from the Ponemon Institute makes this point clear.
According to their report, insiders now account for 60% of corporate data leaks. Worse, insider-led breaches cost twice as much on average than incidents caused by external actors.
Why?
Insiders have legitimate access to corporate assets. That makes it tricky to tell the difference between normal and shady activities.
Moreover, insiders know where to access a company’s most valuable assets. So when they are responsible for a breach, they can inflict more damage.
But even non-malicious actors can pose a risk.
For example, an employee might post a picture of their ID card on social media. Criminals could use these photos to create replica badges. That would make it easy to access secured facilities.
Alternatively, a contractor could store sensitive customer data on an unsecured cloud server. If that fell into the wrong hands, it could result in an expensive and embarrassing breach.
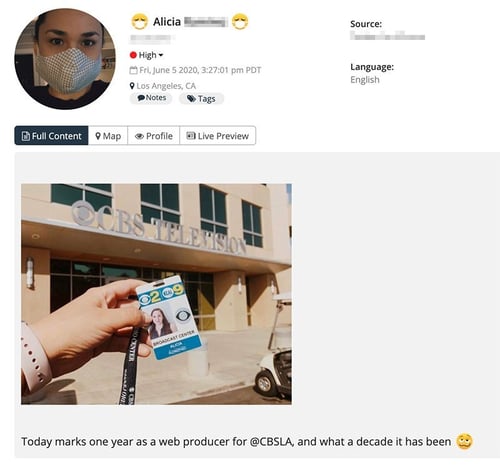
An employee posting their ID card on social media, discovered by Navigator.
So what can organizations do to catch insider threats?
The key here is speed. The quicker you spot a bad actor, the less damage they can inflict.
And sometimes, a fast response may allow you to avoid a serious incident altogether.
Once again, threat intelligence can play an important role.
It takes a number of internal and external feeds to detect threats. The wider your coverage, the less likely you are to overlook a mole hidden in your ranks.
Here’re some best practices:
Behaviour: Watch out for unusual behaviours in the office or at the worksite. Has an employee skipped paid vacation days? Do they visit the office at odd hours? Do they have a bad attitude towards colleagues? None of these red flags alone indicate a worker may be a security risk. But if an individual displays multiple warning signs, it warrants further investigation.
Social Media: Many accidental security breaches, as shown above, happen on social networks. These platforms can also reveal disgruntled workers that could pose a threat. Always watch mainstream sites, like Twitter, Reddit, and Instagram. But also keep an eye on the growing number of “alt-tech” networks, such as Gab and Parler.
Dark Web Forums: Insiders often use dark web forums to promote criminal services, such as deploying malware or selling uniforms. Look out for mentions of your company’s name alongside products and staff members.
Online Marketplaces: Employee theft has surged in recent years due to less supervision and poor screening. This presents an especially big problem for retailers. Insiders often attempt to sell stolen merchandise on marketplaces like eBay or Craigslist. Check for postings of your company’s products alongside phrases like “unused” or “unboxed.”
Internal Networks: Look out for suspicious activity on internal I.T. networks. Does an employee store data on external devices? Have they copied data from sensitive folders? Have they emailed important documents to outside parties? All of these activities warrant further investigation.
Read More:
What are Insider Threats (and How to Detect Them)
5 Times People Missed the Memo on Privacy & Data Security
-
Executive Protection
At LifeRaft, we know from talking with clients that safeguarding VIPs has become a big part of their jobs.
Executive protection once meant hiring a few beefy guys in suits. The job meant having a keen eye and a quick trigger finger.
But today, high-profile executives face a growing number of violent threats. So such a reactivate approach no longer cuts it. Worse, VIPs face more dangers online.
Protection teams also now deal with issues like doxxings and harassment. And increasingly, these virtual threats now present real-world security risks.
So how can you better address these mounting challenges?
Threat intelligence helps protection teams by spotting risks ahead of time. Without intelligence, you can only respond to dangers right in front of you. And once an incident has occurred, it can be tough to regain control of the situation.
But with the right information on hand, agents can deter threat actors. Or better yet, avoid incidents altogether. In either event, this better ensures the safety of the client.
Take the example of a celebrity bodyguard.
I’m sure you’ve opened a gossip tabloid at some point. On occasion, they’ll feature photos of raging fans mobbing a VIP.
In many cases, this means the security detail failed to gather intelligence ahead of time. And by extension, exposed their client to a dangerous situation.
But this scenario could have been prevented with threat intelligence.
An experienced team would have scoped out the venue in advance. By mapping out entry and exit routes, they could then escort their VIP to the destination safely.
Alternatively, the protection team may have noticed suspicious chatter on social media.
Perhaps details leaked about a private event their client plans to visit. In such a situation, security could request a new venue, change travel plans, or cancel the event altogether.
Both scenarios result in the same outcome.
Threat intelligence means sidestepping a potentially dangerous situation. And by extension, ensuring the safety of their VIP.
Increasingly, however, executives and VIPs face a growing number of virtual threats.
Take doxxings, for instance. This is the practice of posting an individual’s personal information without their consent.
Leaked info could include passwords, addresses, medical records, or credit card details.
Obviously, this represents an effective way to humiliate and intimidate victims. And if it happens to a high-ranking staff member, such actions can damage the organization’s reputation.
But doxxings present a serious physical security risk, too.
For instance, threat actors might exploit data gleaned from a leak to harass a VIP’s family members. Or, criminals might use doxxed information to carry out spear-phishing campaigns.
In such situations, speed plays a critical factor.
For example, you can change a VIP’s credit cards and update their passwords. This mitigates some of the damage bad actors can do while data remains public.
Furthermore, knowing what information is out there can allow you to better allocate resources.
For instance, say doxxers leaked an executive’s home address online. It might make sense to station agents near their house.
Or, perhaps doxxers published a VIP’s private information on a social network. Reporting the content quickly could mean it’s removal before any widespread dissemination.
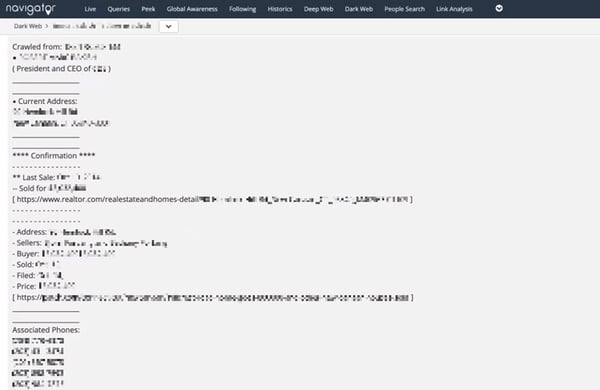
Bottom line: Executives and high-profile individuals represent attractive targets. And the internet gives bad actors more ways to strike.
For those reasons, executive protection teams can no longer rely on a reactive approach. Details must proactively identify and mitigate risks before they present a real threat.
And intelligence serves as the backbone for such a strategy.
Read More:
Executive Protection: 5 Ways Navigator Can Safeguard Your VIPs
-
Event Security
For decades, the fundamentals of event security hadn’t changed: anticipate threats; secure the perimeter; coordinate a skilled team.
But increasingly, organizations have started using a new tactic to safeguard venues: exploiting threat intelligence gathered from social media.
Event staff have to manage a growing number of complex risks. That could include everything from theft and trespassers to gunmen and weather. But now that everyone carries a smartphone in their pocket, these incidents often pop up first on social channels.
Moreover, security teams now deal with new digital headaches, too.
An onlooker could leak a VIP’s location on TikTok. Bad actors might post death threats on Parler. And such virtual risks can present very real-world threats.
Sure, these platforms remain mostly in the domain of marketing departments.
But more and more, you’re likely to see a Twitter or Facebook dashboard in the security operations center.
That’s because these platforms offer a number of ways to keep attendees safe.
For example:
- Anticipate Risks: Intelligence from online chatter can allow you to spot bad actors planning to disrupt your event. That in turn gives security leaders more info to better deploy their resources.
- Spot Threats: Any number of incidents could occur before an on-the-ground team member takes notice. And if left unchecked, these events can escalate quickly. Often, however, bystanders report disruptions on social media. If an analyst spots something online, they can alert colleagues.
- Locate Incidents: Figuring out where a threat originates from presents a challenge. This is especially true at large venues, like concerts or convention centers. But geo-tagged data allows staff to locate incidents quickly.
- Spot Data Leaks: Events, surprisingly, rank as one of the most common sources of data leaks. It only takes one onlooker posting a clip to spoil an announcement or divulge trade secrets. These breaches present a real physical security risk, too.
Professional sport teams, in particular, have embraced threat intelligence to safeguard their events.
In 2013, the NFL’s Minnesota Vikings played their final game at the Metrodome Stadium. But ahead of the event, security teams picked up troubling online chatter. Some fans had started planning a postgame fieldrush after the fourth-quarter.
Team security director Jeff Spoerndle took the threat seriously. In 1981, Vikings fans stormed the field after the last game at Metropolitan Stadium. That resulted in widespread theft, looting, and injuries.
So ahead of the event, security added extra guards fieldside. That foiled fan efforts to wreak havoc after the game and ensured a safe evening for everyone.
“[Threat intelligence] allowed us to have an idea of what was going on in the mindset of people in the building,” Spoerndle told the Associated Press.
Even college-level teams have started gathering threat intelligence for physical security.
The NCAA, for instance, often scans social media ahead of big events like the Final Four. Staff members keep a look out for fans that have posted photos of ticket stubs. Alternatively, they may spot journalists that have published images of their press credentials.
That presents a big problem for the NCAA. Criminals could use these pictures to create fraudulent tickets. Or, trespassers could print fake credentials to access secured facilities.
But after spotting such images, the NCAA’s social team will simply ask posters to take them down. Most people are thankful for the reminder.
Of course, threat intelligence won’t replace traditional forms of security.
Venues still rely on guards to look out for suspicious activity. And you still need people on the ground to address incidents and deter bad actors.
Still, a single analyst online has enormous leverage to spot threats. That can go a long way towards ensuring a small incident doesn’t escalate into a bigger issue.
And ultimately, that keeps everyone safe.
Read More:
5 Ways to Use Social Media for Event Security
-
SECTION 4:
Scaling Your Threat Intelligence Program
The 5 Traits of a Successful Threat Intelligence Program
At LifeRaft, we’ve helped hundreds of customers set-up and expand their threat intelligence programs.
Through this process, we’ve identified a handful of traits common across successful initiatives.
And the faster companies archived these milestones, the quicker they started to see a payoff from their investment.
Start Small: Building a complete threat intelligence program represents a huge task. But you don’t need to do everything at once. Look at the security needs of your organization. Seek out a few free tools. Then start watching a handful of relevant data feeds (i.e. social media, online marketplaces, internal network logs, etc). Over time, you can add more resources and technology as needed.
Get Quick Wins: Executives and board members want to see tangible benefits from their security investment. Thankfully, you probably don’t need to add much in the way of apps or staff to start delivering results. For example, you could spot stolen inventory by scanning social media for mentions of your company’s products. Or perhaps you can discover leaked account credentials circulating on the dark web. Getting a quick win will go a long way to earning buy-in from other stakeholders.
Automate: Right from the beginning, smart intelligence teams automate routine processes. This starts with foundational tasks like parsing, normalizing, and indexing raw data. Over time, this should also include high level activities like reporting and incident response. The payoff from these efforts? The more you automate, the more time you free up to make smart, informed decisions.
Focus: All businesses, regardless of size, have limited security resources. That’s why it’s critical for teams to outline a plan upfront. What are the most valuable assets we need to defend? Who or what represents the most serious risk to the organization? Identify and rank priorities accordingly. That way, your company can stretch a limited budget for maximum effectiveness.
Stay Up to Date: Firms often get into a habit of publishing reports to address yesterday’s hazards. Unfortunately, the threat landscape keeps changing. And bad actors continue to devise new techniques. Don’t worry, therefore, about hitting report deadlines or sticking to a publishing schedule. It’s far more important to stay up to date on the latest security news and best practices.
Threat Intelligence Solutions
At some point, a threat intelligence program for physical security will need to grow beyond free tools and resources.
The internet is a big place.
A threat could emerge on any number of forums, paste sites, or social networks. You can’t watch every nook and cranny of the web 24/7.
Alert fatigue presents another problem.
More feeds mean pouring through more data. Spotting a real threat amid terabytes of info is like searching for that needle in the proverbial haystack.
For many teams, threat intelligence software provides an answer to these headaches.
Firstly, these systems usually grant you access to a wider variety of data feeds. They also make it easier to access parts of the net often off-limits to normal browsers, such as the dark web.
Second, software can automate routine processes. This frees you and your team members up to handle other tasks.
Finally, different solutions can assist with different parts of your threat intelligence lifecycle.
Some tools, for instance, automate data collection and processing. Others deliver “cooked data,” or finished intelligence, for their customers.
No single piece of software, of course, represents a “silver bullet.”
Instead, savvy teams put together a collection of tools in their tech stack. And these tools will vary depending on the needs of their business.
But regardless of your requirements, any tool should meet the following guidelines:
- Organizational Fit: Big firms usually have a big physical footprint. And that means a large number of assets to defend. So enterprises may need more complex, robust software. A smaller business, in contrast, can probably make do with a simple, inexpensive system.
- Wide Coverage: The more data sources you track, the less likely you are to overlook a threat. Intelligence software should include data feeds across the surface, deep, and dark web. Teams should also be able to watch and analyze these feeds on a single platform.
- Customizable: General industry information isn’t enough. An intelligence solution should allow you to scan for threats targeted specifically at your organization. That will allow you to spot incidents, such as data leaks, violent threats, and viral misinformation.
- Investigative Capabilities: Most intelligence software simply aggregates data. Or perhaps it allows users to run keyword queries to flag posts. An effective solution, however, should allow analysts to dive deeper and investigate content. Only by connecting many data points can your team derive actionable insights.
- Address Alert Fatigue: The sheer number of alerts and alarms can overwhelm analysts. Effective threat intelligence tools should filter out irrelevant information and false positives.
- Intuitive User Interface: Vendors often design their software with the advanced analyst in mind. Unfortunately, this results in complex tools with a high learning curve. And for your team, that means investing days or weeks training employees. A good solution should, therefore, have a simple, intuitive user interface. That cuts the amount of time and money organizations have to spend on training.
“Intelligence analysts are very busy people. They are constantly searching for threats, validating, and communicating. Using multiple tools to do this slows down that workflow. Every time an analyst transitions to a new tool, they need to switch gears and think about a new workflow. Having a unified tool reduces the breaks in that process and creates breathing space. This enables a faster transition from threat validation to communication.”
— Neil Spencer, Product Manager LifeRaft, Inc.
A Final Word on Threat Intelligence for Physical Security
Today, your team probably faces a swath of different challenges — protecting worksites, deterring thieves, safeguarding supply chains, watching out for data leaks.
On top of all that, the industry grapples with a shortage of skilled talent. Security represents a stressful job. Important decisions get made each day. In other words, not your entry-level gig for a new college grad.
Threat Intelligence for physical security can potentially address both of these problems.
By looking out for risks, your team can mitigate threats and respond faster to incidents. The end result is stretching limited security budgets for maximum effectiveness.
And ultimately, that means keeping your customers, personnel, and property safe.

