use cases
Navigator for Threat Actor Investigations & Case Management
As a corporate security analyst, finding and understanding the individuals and groups that pose a threat is critical to protecting your organization.
Threat actors are constantly evolving their tactics and strategies, making it difficult for companies to have the context they need to reduce potential risks. With the right tools, organizations can now find intelligent solutions that quickly respond to threats.
How Navigator Threat Intelligence & Case Management Solutions can help with Investigations
- Uncover the online footprint of a threat actor
- Associating an online persona with a real-world individual
- Assess the digital history of a threat actor across multiple online sources from surface web to dark web
- Provide automated alerting to understand changes in threat posture
Read a Case Study
Read how the Navigator platform helped quickly identify the digital footprint of a hacker, ultimately saving hundreds of person-hours in manual searching.
Our Case Management Application
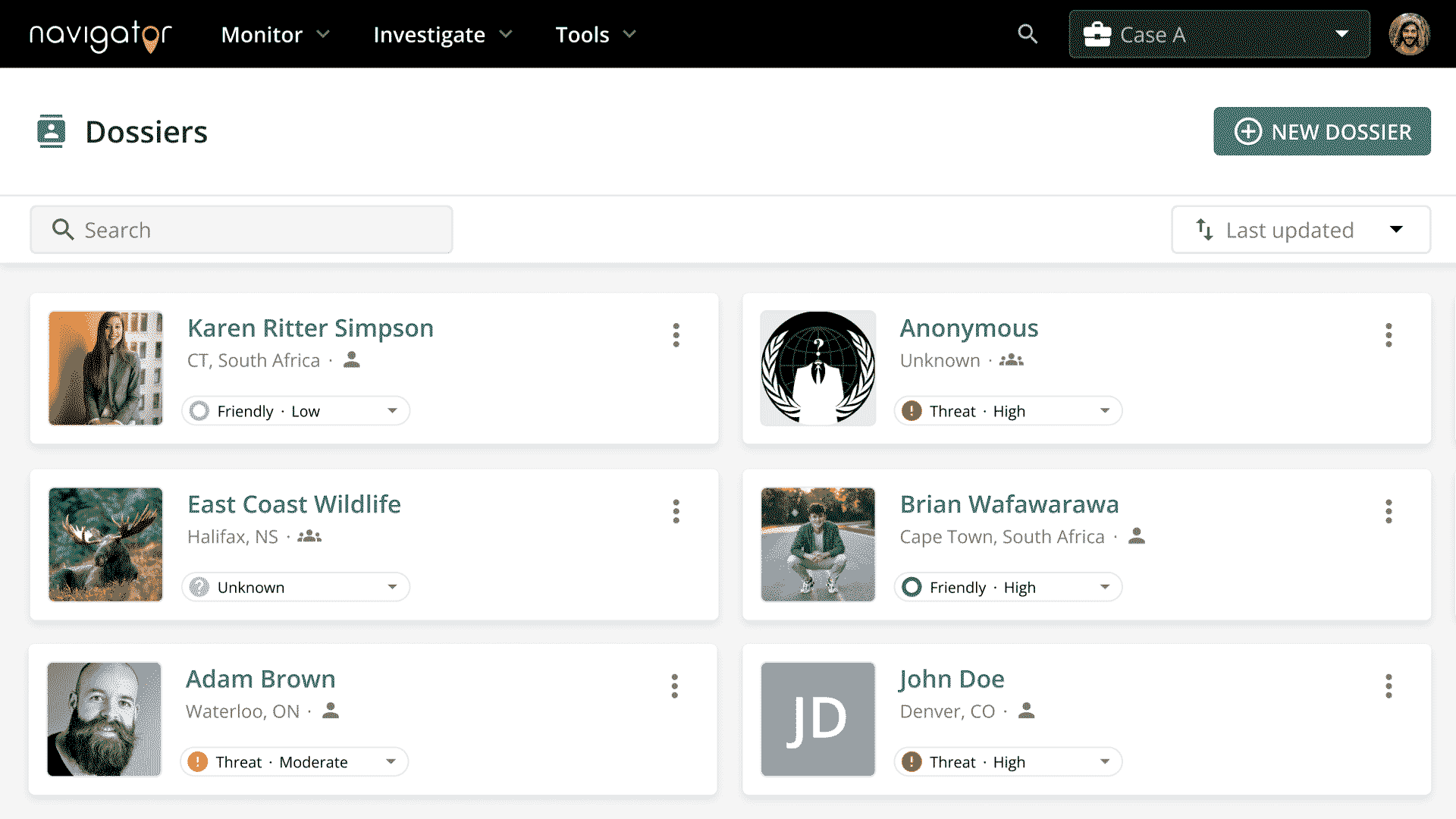
Dossiers
Elevate your investigative process by streamlining your workflow and eliminating the need for multiple systems.
Dossiers provide a unified hub for intelligence discovery, collection, and ongoing management, maximizing efficiency and minimizing complexity.
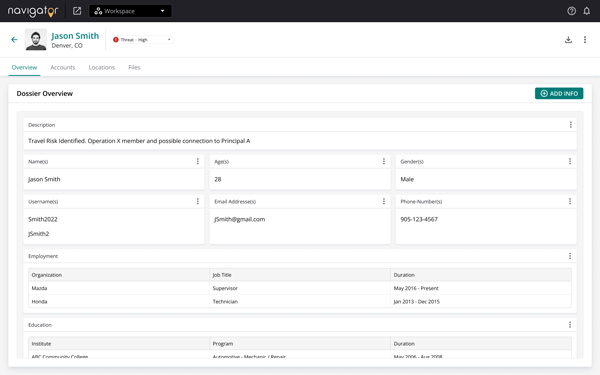
Each individual Dossier serves as a centralized repository, housing valuable information related to your cases, sourced from in-platform results and external file uploads. Experience the power of consolidated intelligence management with Dossiers, driving informed decisions and strategic outcomes.
Key Features
- Centralize PII, locations, social profiles, employment, and other pertinent data for ongoing monitoring, data repository, or investigation.
- Create Group Dossiers in order to facilitate continuous collection, monitoring and management of a Group of Interest.
- Unveil the complex web of connections between Dossiers, with the ability to illustrate and explore relationships among Threats, Principals, and Friendlies.
- Add a timeline activity to track significant events and milestones within your Dossiers and link Queries and Followings for a holistic understanding of the investigative landscape.
- Further enrich your Dossier with the ability to add an Event, providing a centralized hub for all of your Investigative framework. Whether the event is online or in person, you can be sure that every crucial moment and interaction is recorded!
- Escalate and share your Dossiers (incidents and cases) with your crisis management team or enforcement officials.
Related Posts
5 Cognitive Biases That Could Affect Your OSINT Investigations
What is the number one factor that can obstruct OSINT investigations? The answer is probably looking back at you in the mirror. All too many conversations regarding open-source intelligence focus on exciting tools and techniques. A quick Google search for OSINT will reveal endless articles on using such-and-such a system to extract a bounty of data.
SOCMINT: Why is it Important for Security Teams?
In 2013, social media monitoring enabled the NFL’s Minnesota Vikings to thwart a plan for fans to rush the Metrodome Stadium after the game. In response to online chatter hinting that a post-game rush was imminent, the NFL added more security. Sound like an overreaction? Hardly. In 1981, fans stormed the field after the team played their final game at the previous Metropolitan Stadium...
How to Collect OSINT on the Dark Web
At LifeRaft, we know from talking to hundreds of corporate security professionals that many organizations fail to collect open-source intelligence, or OSINT, on the dark web. But this could be a big oversight. In recent years, the dark web has emerged as a hub for criminal activity. And without regular monitoring, security teams could overlook real threats to their business.




