use cases
Navigator for Location & Event-based Threat Monitoring
From political unrest to economic instability and natural disasters, many factors must be considered when monitoring for and managing these threats.
Geopolitical Risk Management
As a corporate security analyst, your organization faces a range of potential geopolitical risks that can impact your operations, employees, and assets.
How Navigator can help with Geopolitical Risk:
- Monitor for physical, cyber, environmental, or situational threats or events that impact business continuity
- Leverage analyst-annotated notices on events around the globe for risk assessments and reporting
- Collect data from local online sources that provides ground truth for emerging or ongoing situations
- Harness curated regional feeds to identify trends and events that will inform decision making
Learn How Security Leaders Use OSINT to Protect Critical Infrastructure
Learn how oil and gas companies use Open Source Intelligence (OSINT) for pipeline security, as well as the challenges and limitations of this approach.
INVESTIGATIVE OPEN SOURCE INTELLIGENCE SOFTWARE
Navigator cuts through the online noise to identify and validate OSINT threats across the broadest range of mainstream and niche data sources. We help companies protect people, assets, and businesses — making the world around us safer every day.
Event Security
As a corporate security professional responsible for event security, you understand the importance of staying ahead of potential threats and ensuring the safety of attendees, staff, and assets.
With an increasing number of potential threats, including extremism, weather events and violence, it is more important than ever to have access to timely intelligence and threat management tools.
How Navigator can help with Event Security:
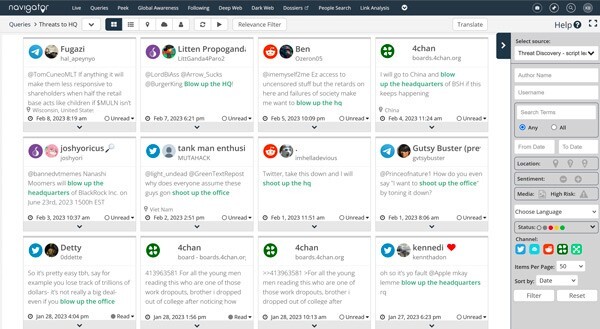
- Investigate known threat actors or uncover key intelligence to conduct identity resolution
- Monitor activity of interest, relating to topics, locations, or online authors of interest
- Set up custom search queries for intelligence relating to intrusions, acts of violence, counterfeit, or other disruptive activity
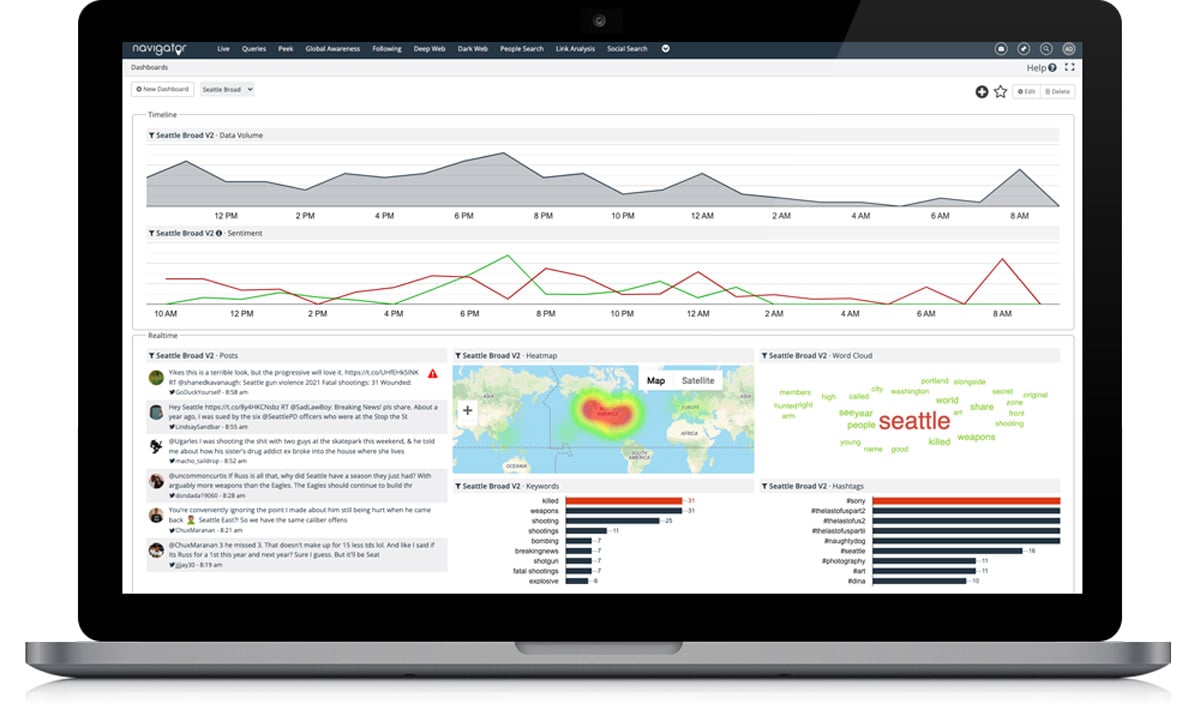
- Analyze custom dashboards with curated threat feeds, dynamic mapping, and high-risk posts for monitoring
- Conduct investigations on networks of interest, connectivity, and relationships to executives or business interests
Panel Discussion: Securing in the Spotlight
Social media monitoring has emerged as a critical tool for security leaders at sport and entertainment venues. By monitoring online platforms, analysts can gain real-time insights into potential threats, including negative sentiment, harassment, and even planned attacks.
Physical Asset Protection
As a security professional responsible for physical asset protection, ensuring the safety of your organization's assets is a top priority.
With a wide range of potential threats, you need the latest information to successfully monitor threats to your physical infrastructure, offices and critical locations.
How Navigator can help with Physical Asset Protection:
- Identify threats of violence or safety-related concerns
- Monitor for severe weather or issues from ongoing global events that could impact the security of your assets
- Be notified of location-based activity that may disrupt your operations based on risk-level or proximity
- Investigate and track niche sources for security intelligence
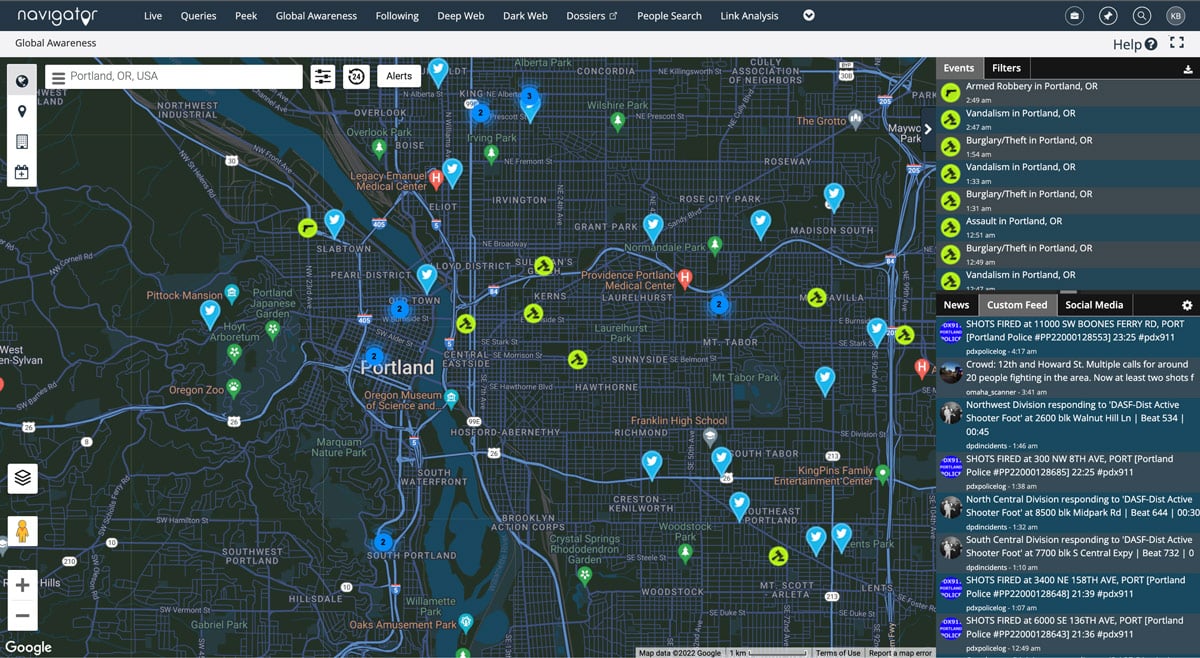
- Display dynamic mapping and data visualization for ease of analysis
Interested in what Navigator can do to help bolster your threat monitoring initiatives?
Event Detection
As a corporate security professional responsible for detecting disruptive events, you need to be able to detect potential events that pose a threat to your business operations before they escalate.
How Navigator can help with Event Detection:
- Analyzing social media to identify emerging posts that could signal a disruptive event
- Analyze location-based and inferred data, providing insights into potential threats in specific areas
- Harness curated localized social media feeds to identify events that emergency services and news sources are reporting
- Display dynamic mapping and data visualization for ease of analysis
- Automating alerts to inform security teams and stakeholders of emerging events
- Providing context and ongoing validation following the initial event detection
Related Posts
5 Ways to Use Social Media for Event Security
If you’re an event security professional, then you have a lot on your plate. Teams have to spot and manage all kinds of different risks. That could include everything from trespassers and theft to gunmen and weather. Moreover, personnel now deal with more digital headaches, too. Bad actors might post threats on Gab. An onlooker could leak a VIP’s location on Twitter.
What Businesses Need to Know About OSINT for Physical Security
Cybersecurity practitioners have long exploited open-source intelligence, or OSINT, to safeguard data. But increasingly, businesses have started to recognize the benefits of OSINT for physical security, too. And for good reason. The best OSINT programs help leaders understand what is happening and see around corners to predict what will likely happen next.
5 Ways Energy Companies Can Strengthen Corporate Threat Intelligence
Open-source intelligence (OSINT) is quickly becoming a vital component of corporate threat intelligence for energy companies. In today's digital age, it's no longer enough to install locks and cameras: proper protection from potential threats – both internal and external – demands comprehensive collection and analysis.






