Amidst rising concerns over security threats and potential acts of violence, the Minnesota Vikings showcased how open-source threat intelligence averted a potentially serious incident.
Ahead of the NFL squad’s final home game at the Metrodome Stadium, security analysts spotted chatter on social media indicating some fans had started planning a post game field rush. And officials with Whelan Security, the company hired to manage the team’s venue security, had good reason to be concerned. After the Vikings’ final game in Metropolitan Stadium in 1981, fans rushed the field and swiped anything that hadn’t been bolted down.
But by leveraging open-source threat intelligence, the team’s security details managed to anticipate a potential post game field rush and promptly increased the number of security guards on duty. This effectively thwarted any fans' attempts to disrupt the event, ensuring a safe evening for everyone in attendance.
"It allowed us to have an idea of what was going on in the mindset of the people in the building so we could counteract that," said Jeff Spoerndle, Whelan's director of special services, told the Associated Press in an article about the incident.
The Minnesota Vikings are not alone in their exploitation of open-source threat intelligence to manage risk. In an era marked by dynamic and evolving threats, businesses across industries are increasingly recognizing the instrumental role that open-source threat intelligence plays in fortifying their risk management strategies. Leveraging publicly available data and insights, organizations can proactively identify potential risks such as cyber threats, political unrest, or economic uncertainties.
This shift towards harnessing open-source intelligence empowers businesses to stay ahead of emerging challenges, enabling informed decision-making and the implementation of preventative measures. As the corporate landscape continues to grapple with an array of potential threats, the adoption of open-source threat intelligence emerges as a critical component in the arsenal of tools that companies deploy to safeguard their operations, reputation, and overall resilience.
What is Open Source Threat Intelligence?
In recent years, open-source threat intelligence has taken center stage as an innovative and indispensable facet of risk management. Picture it as a sophisticated radar scanning the vast horizon of publicly available sources—social media, forums, and diverse data streams—to anticipate potential risks. This approach involves the strategic extraction of insights from these outlets, offering a panoramic view of potential risks that businesses and organizations might encounter. Embracing a proactive stance, open-source threat intelligence transcends conventional security measures, allowing entities to anticipate and navigate an array of challenges.
The field marks a paradigm shift in the realm of risk mitigation by challenging the historical reactive approach to security. Traditionally, companies have been compelled to respond to security threats as they emerge, often playing catch-up to cyber adversaries. However, with the advent of open-source threat intelligence, businesses can proactively identify and address potential risks before they materialize.
By leveraging insights gleaned from publicly available sources, ranging from social media to diverse data streams, organizations gain the ability to foresee and comprehend emerging threats. This proactive stance not only empowers companies to stay ahead of potential risks but also transforms the security landscape from a responsive model to one of anticipatory readiness, allowing businesses to implement preemptive measures and foster a more resilient security posture.
Open-source threat intelligence has proven invaluable in enhancing physical security across various domains. From critical infrastructure protection to event security, its use cases are diverse and impactful. In the realm of critical infrastructure, businesses can leverage open-source threat intelligence to monitor and preemptively address potential vulnerabilities, ensuring the robust safeguarding of facilities against physical threats. In event security, the technology can be employed to analyze publicly available information, such as social media, to anticipate crowd behavior and mitigate potential risks before they escalate. Additionally, open-source threat intelligence aids in securing supply chains by monitoring global events and geopolitical developments that could impact physical assets.
A recent incident at Amazon underscores this point. In a swift and coordinated effort, the tech giant successfully thwarted a potential threat to one of its data centers in Virginia after authorities uncovered alarming posts on MyMilitia.com, a forum dedicated to militia organization. The investigation was triggered by the Texan suspect, operating under the handle Dionysus, who expressed discontent with Amazon's decision to sever ties with Parler, a social network associated with extremist content and linked to the January 6 attack. Making clear his intentions not to become a "dumbass suicide bomber," Dionysus proclaimed a willingness to sacrifice himself to prevent perceived injustices against fellow Americans. Amazon, quick to respond to the potential danger, collaborated closely with the FBI to investigate and ultimately apprehend the suspect could launch any attack on the data center.
The NCAA also employs social media monitoring as a crucial strategy to protect the integrity of its events and the interests of both fans and ticket providers. By actively scanning social media platforms, particularly during high-profile events like the Final Four, the NCAA can swiftly detect posts containing images of tickets or media credentials.
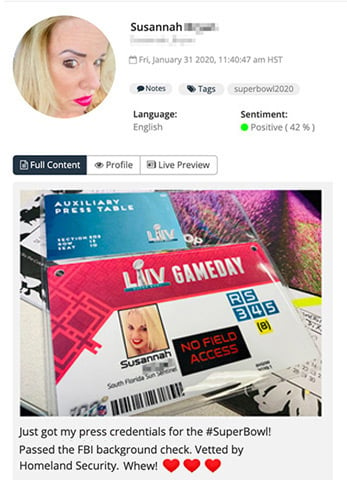 A journalist posting an image of their press credentials to social media, discovered by Navigator.
A journalist posting an image of their press credentials to social media, discovered by Navigator.
Identifying information has been redacted.
This proactive approach allows the organization to engage with individuals sharing such content, urging them to remove it promptly. The primary goal is to mitigate the risk of fraudulent activities, such as the production of counterfeit tickets or credentials based on publicly shared images. This diligent monitoring not only safeguards the NCAA's events against potential security threats but also serves as a preventative measure to ensure a secure and enjoyable experience for all stakeholders involved.
In addition to physical risks, corporate security teams also exploit open source threat intelligence to mitigate cybersecurity threats. Such a proactive approach allows businesses to anticipate and counteract a swath of different malicious activities: identifying potential phishing schemes, predicting malware outbreaks, identifying potential insider threats, spotting system vulnerabilities, and thwarting advanced persistent threats (APTs) before they infiltrate networks. Through the lens of open source intelligence, organizations gain insights into global cyber landscapes, enabling them to bolster their defenses against evolving threats.
The Growing Value of Open Source Threat Intelligence
Traditionally, in-house intelligence functions were primarily associated with bolstering security. In recent years, however, businesses have undergone a paradigm shift in their approach as executives now recognize the broader value of open source threat intelligence. As highlighted in the article, such departments not only aid in identifying and addressing security risks but also spotting trends and opportunities for the company as a whole. Today, leveraging open source threat intelligence represents a serious competitive advantage, allowing businesses to stay ahead in an ever-evolving landscape.
Fiserv's proactive response to the COVID-19 stands as a testament to the crucial role of open source threat intelligence. By triangulating information from reliable sources at the very start of the pandemic, the financial technology company’s in-house intelligence team accurately anticipated the potential impact of the virus. This early insight empowered Fiserv to recommend precautionary measures, such as limiting executive travel and investing in protective equipment. The result was a swift and effective transition to remote work, showcasing the strategic use of open source threat intelligence in adapting to unforeseen business threats.
Open source threat intelligence also equips businesses to operate in high-threat environments where others fear to operate. In such environments, businesses can strategically allocate resources, avoiding unnecessary expenses on security measures. Intelligence can also prevent overreactions to potential incidents.
Microsoft's experience in the aftermath of Hurricane Maria illustrates how open source threat intelligence contributes to confident decision-making. Faced with alarming external reports about security dangers in Puerto Rico, executives considered halting all travel to the territory. Microsoft's in-house intelligence team, however, managed to provide a nuanced assessment of the company’s risk profile tailored to the organization’s specific footprint. This intelligence-driven analysis gave the company's leadership the confidence to continue operations in the area safely.
How to Conduct Effective Open Source Threat Intelligence
Users upload terabytes of content to the web every minute, representing an enormous pool of information. But despite this wealth of data, security teams must adhere to best practices to extract meaningful results. Open source threat intelligence requires a strategic and meticulous approach to sift through the vast digital expanse effectively.
Cover Your Digital Footprints
While the internet provides a window to watch potential adversaries, adversaries can also use the interest to watch you. Using technologies, such as Virtual Private Networks (VPNs), ensures that their investigative efforts go unnoticed by outsiders. By masking your online presence, you can operate covertly, reducing the risk of interference and maintaining the integrity of their investigations.
Document Your Findings
Security teams should prioritize meticulous documentation during investigations due to the ephemeral nature of online information. The digital landscape is dynamic, and data discovered today may vanish tomorrow. By thoroughly documenting findings, security teams create a crucial record that not only aids in understanding the current threat landscape but also serves as a historical reference. This documentation ensures the preservation of critical insights, evidence, and context, enabling the team to reconstruct the timeline of events and maintain a comprehensive understanding of the evolving threat landscape.
Cast a Wide Net for Data Collection
To maximize the scope of open source threat intelligence, it is crucial to cast a wide net for data collection. Beyond mainstream social networks, analysts should explore lesser-known alt-tech social networks and delve into the depths of the dark web. This expansive approach ensures a comprehensive understanding of potential threats, uncovering patterns and connections that might be overlooked in more conventional sources.
Exploit Automation Tools
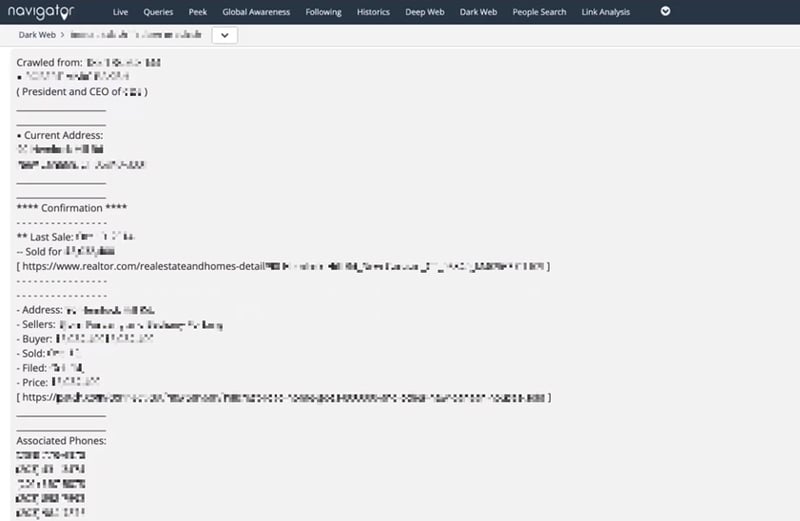 Leaked personal information of a senior executive on the darknet, including wi-fi passwords, home address, and family member details, discovered by Navigator. Identifying information has been redacted.
Leaked personal information of a senior executive on the darknet, including wi-fi passwords, home address, and family member details, discovered by Navigator. Identifying information has been redacted.
Automation tools, such as LifeRaft Navigator, provide immense value in the realm of open source threat intelligence. The fifth tip underscores the significance of leveraging automation to streamline data collection and routine tasks. By automating repetitive processes, security teams can allocate resources more efficiently, allowing analysts to focus on in-depth analysis and decision-making rather than being bogged down by manual tasks. Automation enhances the speed and accuracy of threat intelligence, empowering organizations to stay ahead in the ever-evolving cybersecurity landscape.
The Bottom Line
Embracing threat intelligence is not just a strategic choice for companies; it is a fundamental necessity in today's complex and ever-evolving security landscape. The collaborative nature of open source communities fosters innovation and accelerates the development of effective threat intelligence solutions. By leveraging shared knowledge, organizations can proactively identify and mitigate risks, fortifying their security defenses. The democratization of threat intelligence not only empowers companies of all sizes but also contributes to the collective resilience of the entire digital ecosystem. As we navigate the dynamic challenges of space, open source threat intelligence emerges as a crucial ally, enabling companies to stay ahead of threats, adapt to emerging risks, and ultimately safeguard their digital assets and reputation.
