Social Engineering, in the context of security, refers to manipulating people into performing actions or divulging confidential information. It is popular because, in theory, it is easier to trick someone into giving you their information, than hacking a network.
In this digital age, traditional security attacks are leveraging social engineering tactics to be even more effective. It’s a tactic used often in real life and in the movies.
The more you know about social engineering tactics, the better you can protect yourself, your personal information, and your company’s security.
Here we break down some common examples of social engineering with some of our favourite movies.
A convincing email asking for your bank information
Phishing is the most common type of social engineering attack. The attacker recreates the website or support page of a renowned company and sends their targets the link via emails or social media. The intent is that the target ends up compromising personal data (such as credit card information).
In 2015’s Blackhat, hackers send a phishing email to their target organization. They ask employees to change their password and download a PDF, which installs a keylogger in the process. While some movie “hacks” can be a stretch from reality, experts agree this attack is entirely plausible.
 Nicholas Hathaway (Chris Hemsworth) sends infected phishing emails to a target in the movie Blackhat (2015).
Nicholas Hathaway (Chris Hemsworth) sends infected phishing emails to a target in the movie Blackhat (2015).
You can prevent damage from phishing emails by using spam filters in your email accounts, and not opening any emails from an untrusted or suspicious source.
A unique email from your boss asking for money
Similar to Phishing, Spear Phishing requires extra effort from the attackers. They need to pay attention to the degree of uniqueness for the limited number of users they will target.
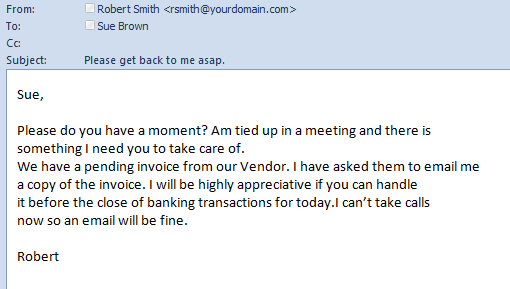 Example of a Spear Phishing from a Boss’s email.
Example of a Spear Phishing from a Boss’s email.
Hard work pays off as the chances of users falling for the false emails are considerably higher (an average of 4 emails sent per stolen credential).
It comes in the form of an email, often from your domain name making it very convincing. Prevent this by not replying. Forward the email to your boss to verify it isn’t them.
A convincing call from the bank that asks you to verify your identity
Many imposters prefer to reach their targets the old fashioned way – by telephone. This type of social engineering attack is known as Vishing.
More than just manual calls, attackers have been known to recreate the IVR (Interactive Voice Response) system of a company. They attach it to a toll-free number and trick people into calling back to enter their details.
Prevent damages by fact-checking the bank number the IVR tells you to call; make sure it is your bank. Likely, you won’t be getting these calls from your bank, anyway.
You probably remember in Ferris Bueller’s Day Off, when Cameron convinces Principal Rooney to release Sloane from school by pretending to be her angry father on the phone.

Like Cameron’s phone call, not all vishing scams are automated. Sometimes the human element of a convincing conversation makes us drop our guard to give up important information.
An unexpected e-mail saying that a maintenance worker will be swinging by
Pretexting is when an attacker presents a fabricated scenario and impersonates a company or service.
Think of Home Alone when Harry impersonates a police officer to perform reconnaissance of the property. Later Harry and Marv impersonate a plumbing and heating company to try and gain access into the home.
 “Home alone” criminals use social engineering to try and gain access into the McAllister house.
“Home alone” criminals use social engineering to try and gain access into the McAllister house.
Another example of pretexting could be fake emails from your distant friend in need of money. Someone may have hacked their account or created a fake one.
A USB drive found in your office bathroom – or in 2019, software links
In the past, Baiting attackers leave infected USB drives in public places with the hope of someone picking it up and using it on their own devices.
A modern example of baiting can be found on the web. Various download links containing malicious software are shown to random users in hopes that someone will click them.

Don’t fall for the old tricks, a found USB probably isn’t worth the money saved! As for software links, exit your browser to avoid any pop-ups.
A delivery driver asks you to hold the security door for them
Another social engineering technique is known as Tailgating. An unauthorized person takes advantage of an authorized person to gain access to restricted areas. These areas have physical or electronic authentications required to gain access.
Be mindful of your perimeters and simply refer the unauthorized individual to security if they try to tailgate.
You’ve probably seen tailgating attacks carried out by Hollywood action heroes like in movies such as Sneakers. When Bishop (played by Robert Redford) works with a delivery man to rush past security without proper identification.
 Bishop Tailgates a delivery man to gain unauthorized access to the organization in “Sneakers” (1992)
Bishop Tailgates a delivery man to gain unauthorized access to the organization in “Sneakers” (1992)
IT calls for an issue that you may (or may not) have
Quid Pro Quo social engineering method involves people posing as support or as a service. They make random calls to a company’s employees claiming they are calling regarding a known (or unknown) issue.
Sometimes, attackers get the chance to make the victim carry out actions for them. Quid pro quo usually involves an exchange of something with the target. This may be access to a discount or solving a victim’s problem.
Hey, what’s your password?
You’re likely to say, “um, no” to this question at first. But if someone follows it up with a question about what makes up your passwords, and you answer with “my favourite color and my dogs name.” Later in the conversation, you may give away that information without realizing. And now they have all the information they need.
Here’s a great video clip from Jimmy Kimmel Live where they surprisingly convince many people to give away their passwords.
A small percentage of the population is likely to experience this. Therefore, those with access to sensitive company or financial information should be aware of this tactic.
Anyone with a social footprint (social media, blog, reddit account) is exposing themselves to social engineering. So, it’s important to be aware of what you’re saying and where you’re posting.
