For decades, open source intelligence, or OSINT, remained in the purview of the defense and intelligence community. Few people thought much about using OSINT for corporate security.
Things have changed.
Thanks to the rapid growth of public data, OSINT has now established itself as an indispensable tool for business risk management.
Savvy leaders, in fact, have even gone so far as to invest in entire OSINT teams dedicated to keeping an eye out for potential threats.
And those investments have paid off. For instance…
- In 2013, the NFL’s Minnesota Vikings discovered a group of fans planning online to rush the field at an upcoming game. Security staff successfully averted a potential riot by adding extra personnel for the event.
- In early-January 2020, the corporate security team at Fiserv advised against executive travel to China after initial reports of a disease outbreak. They made this recommendation weeks before most U.S. companies even acknowledged COVID-19.
- In 2021, a political extremist posted plans online to bomb an Amazon data center. Company officials alerted law enforcement of the looming threat, thereby preventing an attack.
In other words, leaders have realized that a small investment in open source intelligence upfront is far cheaper than responding to an unexpected event down the road.
Still, most companies fail to exploit OSINT to its full potential. And many security leaders don’t consider a potential use case until after an incident occurs.
All of which begs the question, “How can organizations fully exploit open source intelligence for corporate security?”
Let’s take a look at some examples.
Learn More: 5 Cognitive Biases That Could Affect Your OSINT Investigations
7 Ways to Use OSINT for Corporate Security
| 1. Executive Protection | 5. Data Leak Detection |
| 2. Crisis Response | 6. Supply Chain Protection |
| 3. IP Protection | 7. Event Security |
| 4. Loss Prevention |
1. Executive Protection
OSINT has become an essential tool for organizations to safeguard VIPs, such as executives or other high-profile employees.
For instance, security details can scan open sources to spot travel risks and emerging events.
Such situational awareness enables protectors to avoid dangerous areas, set up alternative travel plans, or respond quickly to incidents.
Additionally, high-profile individuals are often subject to violent threats online.
OSINT tools allow details to monitor for threatening posts with phrases like ‘shoot,’ ‘harm,’ or ‘kill,’ alongside the protectee’s name.
If they spot a suspicious post, teams can exploit open source intelligence to gauge the credibility of a threat.
And in the event such posts spark serious concern, protectors can put out a BOLO alert for a person of interest.
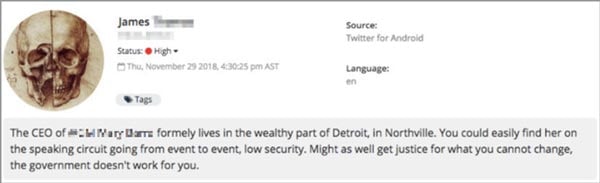 A threatening post directed towards a senior executive of a Fortune 500 company, discovered by Navigator.
A threatening post directed towards a senior executive of a Fortune 500 company, discovered by Navigator.
OSINT's value, however, goes beyond travel safety or violent threats.
Take false rumors spreading online, for instance.
Misinformation could damage a VIP’s reputation, their ability to conduct business, or the value of the organization they represent.
And if left unchecked, misinformation could represent a serious danger to your principal.
Imagine false reports suggesting your company has planned a hostile takeover of a rival firm. Such rumors could incite anger, putting executives at higher risk of an attack.
Keeping tabs on any rumors or false reports allow corporate security teams to respond quickly.
This makes it much easier for organizations to plan an appropriate response. And by extension, this limits the damage misinformation can inflict on the protectee.
Alternatively, open source intelligence can help avoid overreactions to perceived threats.
Take the aftermath of Hurricane Maria in 2017, for example. After reading alarming news reports, Microsoft managers reconsidered their travel plans to Puerto Rico.
The software giant's intelligence team, however, prepared an assessment of the situation for C-suite executives.
They concluded media outlets had painted a misleading picture of the security situation in the terrority.
Moreover, the team believed Microsoft executives would face few serious risks to their well-being in the specific areas they needed to travel.
This gave management enough confidence to operate safely in the area.
2. Crisis Response
Corporate security teams have to contend with three types of hazards:
- Natural hazards. These include extreme weather events such as floods, earthquakes, and blizzards. Other risks, such as infectious diseases or food contamination, also fall into this category.
- Technological hazards. These include power loss, industrial accidents, and infrastructure failures.
- Human-caused hazards. These include riots, cyber-attacks, terrorist threats, or workplace violence.
Such hazards can strike at any time. But corporate security teams face two more challenges in crisis response.
Firstly, a slow reaction time could cost an organization millions in damages or business disruption. A delayed response might also endanger the lives of customers and employees.
Furthermore, many organizations have people and assets scattered around the world.
Even the most well-staffed security teams can struggle to keep tabs on events happening in every place where their company operates.
Thankfully, OSINT solutions can go a long way towards addressing these challenges.
For starters, it’s not uncommon for events to be reported first on social media.
Through continuous monitoring of these channels, corporate security teams can be alerted to a potential crisis hours before reports get picked up by traditional news outlets.
Moreover, reports gathered through open sources often contain firsthand information, such as photos, audio, and comments.
That enables analysts to understand the nature of an incident and respond effectively during a crisis.
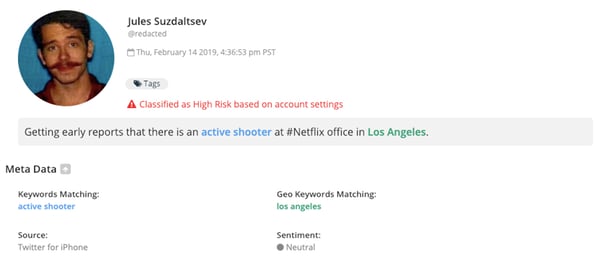
Early reports of an active shooter situation at the headquarters of Netflix, discovered by Navigator.
Disaster relief efforts in Haiti demonstrated the power of OSINT in crisis response.
Following the 2010 earthquake, responders applied geotagged social media posts to identify the hardest-hit neighborhoods.
Rescuers even used this data to pinpoint the locations of people still alive under the rubble of buildings.
And over the following months, such data represented an important tool for NGOs directing recovery efforts.
The OpenStreetMap Project, in particular, represented one of the big success stories from this operation.
Haiti has long ranked as one of the poorest countries in the western hemisphere. As a result, data providers had produced no high-quality maps of the capital city Port-au-Prince.
So when the earthquake struck, crisis responders didn’t have the tools they needed to support victims.
But within hours following the disaster, volunteers created a geo-spatial wiki from tweets and other social media messages.
Within two weeks, the online community created a digital map of the entire country. The information included everything from streets and buildings to parks and hospitals.
All of which proved essential for crisis responders to coordinate operations and distribute aid.
3. IP Protection
Since 2015, 20.0 million Americans have canceled their cable subscriptions. And as more households cut the cord, many have exploited illegal torrents for free content.
Check out these statistics:
A recent study by Synamedia found just over half of sports fans watch illegal streaming services at least once a month.
Furthermore, 29% of fans pay the criminals who operate these channels to access content.
Movie and television studios have the same problem. Online piracy costs the industry as much as $51.0 billion in lost revenue annually, according to estimates by Statista.
Yet despite efforts to crack down on illegal streaming, this figure has only grown year after year.
And as you might have guessed, every dollar that goes to criminals comes straight out of the pockets of leagues and studios.
The sheer size of the internet complicates the problem further.
Pirates can quickly set up new services in obscure corners of the web. That makes it tough to spot and take down illegal content.
Increasingly, however, content producers have started to rely on OSINT tools to combat online piracy.
Security teams often accomplish this by setting up keyword search queries. For example, you might scan for terms like ‘free,’ ‘download,’ and ‘streaming,’’ alongside the name of your brand or intellectual property.
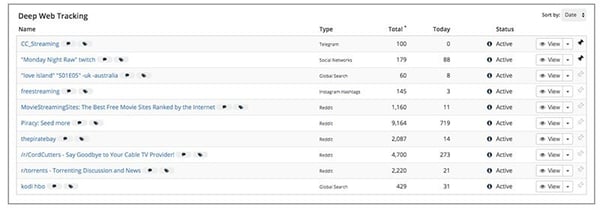 A list of illegal pirate services and torrents, discovered by Navigator.
A list of illegal pirate services and torrents, discovered by Navigator.
After that, these queries will automatically scan for links to illegal streaming services on popular sites like Twitch, Reddit, or YouTube.
Advanced OSINT software can also reveal criminal networks on more obscure corners of the internet, like paste sites or the dark web.
But those responsible for protecting intellectual property can exploit OSINT for far more than just taking down illegal streaming services.
Counterfeiting, for instance, runs rampant on alternative social networks like Telegram. A simple search will reveal an endless number of channels pawning knockoff products from electronics and designer handbags to high-end watches.
An estimated 17% of ebooks are consumed illegally, according to the UK’s Intellectual Property Office. The International Publishers Association estimates online piracy costs authors and publishers billions of dollars each year.
Additionally, malicious insiders often exploit dark web marketplaces to sell closely-held company secrets, such as patents, research plans, or product roadmaps.
Once again, ongoing intelligence gathered from open sources can go a long way towards safeguarding IP.
4. Loss Prevention
If you work in loss prevention, then you are no doubt aware of the growing problem that is organized retail crime.
In the United States, for example, the number of shoplifting incidents nationwide recently hit a 25-year high. And industry experts estimate the average American family will pay an extra $500.00 per year in higher prices to offset the cost of criminal activity.
To combat this trend, more asset protection departments have started to exploit OSINT.
Criminal groups often exploit social media to coordinate robberies or share tips and tactics with their fellow thieves.
Reviewing such discussions can tip off organizations of an organized “flash mob” raid at a nearby store. Or loss prevention teams could learn about a new tactic to evade theft prevention devices.
Take the form Raddle.me, for instance.
The community promotes itself as a group of “outsiders, malcontents and wayward dreamers” while promoting an anarchist, anti-capitalist worldview.
The site resembles a simple version of Reddit. Each form contains ongoing discussions around various topics, such as “Decolonisation,” “AntiWork,” and “EatTheRich.”
Politics aside, keeping tabs on the site can pay off for loss prevention efforts.
For instance, you can find detailed how-to guides for shoplifting at many retail brands on the form /f/Illegalism.
Users also share methods to override anti-theft devices and conceal stolen goods as well as the easiest stores to target.
This type of information amounts to a free security consultation by the very same people stealing from your business.
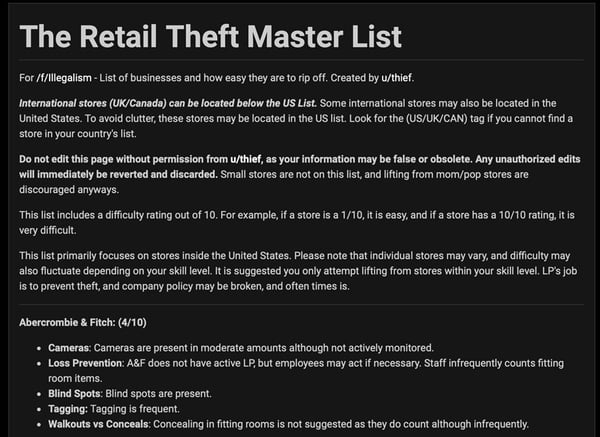
A screenshot of a popular shoplifting guide, discovered by Navigator.
OSINT can also support the recovery efforts.
The days of offloading stolen goods at the local flea market have mostly come to an end. Today, fences prefer to exploit the anonymity and scale of the internet to move merchandise.
Most asset protection teams now actively monitor online marketplaces for stolen goods. But sophisticated OSINT tools can automate this process, alerting investigators as soon a relevant listing pops up.
Furthermore, software vendors can track obscure online communities where criminals gather, such as paste sites, dark web marketplaces, and alt-tech social networks.
All of this information can help retailers adapt in-store security practices, locate suspects during an investigation, and elicit the support of law enforcement.
5. Data Leaks
Data leaks now represent expensive incidents for businesses.
The average cost of a data breach for organizations now tops almost $3.9 million, according to a 2021 survey by IBM.
That number increases to $8.2 million on average per incident for companies based in the United States.
In the study, IBM included the explicit costs of handling a breach: detection, investigation, notifying customers, paying fines, patching software, etc.
But the authors also went further and considered some of the less obvious expenses, such as customer churn and reputational damage, that follows from bad publicity.
If prospects don’t trust your company’s IT security, they may take their business elsewhere.
Data breaches present other types of security risks, too. For example:
- Doxings: Doxing is the act of publishing a person’s private information without their consent. Threat actors may publish this information for a variety of reasons, such as harassing or shaming a particular individual.
- Unwanted Attention: A photo detailing the whereabouts of a VIP to social media could attract unwanted attention from fans, stalkers, or media outlets. This could disrupt an event or business operations. In the worst-case scenario, this type of leak could represent a threat to the safety of a principal.
- Extortion: Data leaks can include sensitive information such as photos, videos, chat logs, and health records. That can make victims targets for extortion.
- Social Engineering: Attackers can exploit seemingly harmless personal information, like names, addresses, and phone numbers, to access other data. Criminals can use this data to pass security screening questions, request account changes, or send fraudulent emails.
- Access Facilities: It’s not uncommon for employees, customers, and other stakeholders to publish pictures of their workplace ID badges or tickets to upcoming events. Criminals can exploit these images to create fake passes and access secured facilities.
OSINT tools allow organizations to spot data breaches on social media or in fringe online communities, such as chan boards, paste sites, and dark web marketplaces, where threat actors sell and share leaked data.
On-going monitoring of these sites allows corporate security teams to respond to such incidents quickly.
And by extension, this intelligence can mitigate the risks to employees and the organization.
6. Supply Chain Protection
You only need to see the empty aisles at retailers in recent months to appreciate the impact of the global supply chain crisis.
The process that delivers a product to store shelves is a tightly interconnected network. If one link in that chain fails — from sourcing and manufacturing to transportation — the whole system breaks down.
And that breakdown can have huge repercussions.
If shelves sit empty, shoppers can’t buy your product. Any supply chain disruptions can result in millions of dollars of lost sales for retailers.
For logistics and transport companies, supply chain havoc can result in missed deadlines for product deliveries.
Short-term, that may result in financial losses. Long-term, such issues could impair the reputation of the entire company.
For supply chain managers, the solution is to have all available information on emerging and current threats.
Sure, new technologies like blockchain and IoT sensors play a role in this process. But OSINT provides extra context that can allow decision-makers to respond more effectively in a crisis.
For example, supply chain managers could exploit OSINT techniques to answer the following questions:
- What is happening around a key factory on the other side of the world?
- What products are out of stock at our retail stores?
- What is the risk of terrorism or piracy on the routes where our ships operate?
- Will an outbreak of COVID-19 shut down a warehouse?
- Will poor weather threaten employee safety and disrupt transportation routes?
- Will a merger between two suppliers impact our ability to source a component?
The stakes are high when it comes to sourcing parts and inventory.
But OSINT tools allow organizations to maintain situational awareness over their entire supply chain.
And by extension, this can allow operators to respond quickly and effectively to emerging events.
7. Event Security
The fundamentals of running a safe event haven’t changed much in decades. But increasingly, savvy venues have started to employ open source intelligence to protect attendees.
In the context of event security, OSINT has several applications. For example:
- Anticipate Risks: Venue operators have no shortage of risks that could disrupt their event: trespassers, rowdy fans, bad weather. Thankfully, intelligence from online chatter can allow you to spot potential problems ahead of time. With that information on hand, security leaders can more effectively deploy resources.
- Continuous Intelligence: Security teams often conduct a threat assessment ahead of an event. Unfortunately, new risks could emerge at any time. OSINT allows teams to spot unexpected threats. This continuous intelligence-gathering represents a far more effective practice than a static, one-off threat assessment.
- Identify Incidents: If staff members cannot promptly spot and address an incident, it could spiral out of control. Thankfully, bystanders often discuss disruptions on social media. A proactive analyst collecting open source intelligence online can spot initial reports and alert colleagues.
- Locate an Incident: Geo-tagged social media posts allow teams to quickly determine where an incident has taken place. At large venues, like concerts, sports stadiums, or convention centers, this represents especially valuable information.
- Spot Data Leaks: It only takes one onlooker posting a photo online to spoil an announcement, divulge trade secrets, or reveal the location of a VIP. Security teams also need to consider members of the public, like fans, staff, or journalists, publishing pictures of their passes to events. As mentioned above, trespassers can use these images to gain unauthorized access to venues.
Sports teams, in particular, have embraced OSINT for venue security.
For example, the NCAA continuously monitors social media ahead of events like the Final Four. Analysts watch for attendees that have posted photos of ticket stubs or press credentials.
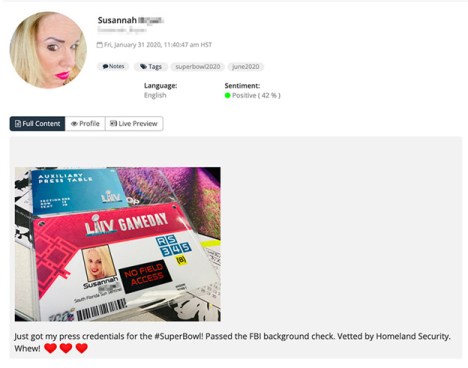 A journalist posting an image of their press credentials to social media, discovered by Navigator.
A journalist posting an image of their press credentials to social media, discovered by Navigator.
After spotting such images, the NCAA’s social media team can ask these individuals to delete their posts. Most fans will comply.
Of course, OSINT won’t replace traditional practices of event security.
Still, a single analyst gathering open source intelligence can represent an enormous force multiplier for a short-staffed detail.
The Bottom Line on OSINT for Corporate Security
Organizations have finally started to appreciate the value of OSINT for corporate security.
Businesses understand it’s far better to make a small investment upfront gathering intelligence than being caught flat-footed and responding to an incident after the fact.
Still, most security teams have not exploited all the value they can from open source intelligence.
The solution to this problem comes down to awareness.
In many cases, teams don’t need to invest in expensive training. It can be helpful to simply take the time to understand how other their peers exploit these OSINT techniques for new applications in their own organization.

