Images posted online can reveal a lot more than you might think.
Every time you snap a photo, your smartphone or digital camera records a wealth of information: the type of camera used, settings the photographer selected, when and where the photo was taken. It’s called EXIF data.
And this information travels everywhere with your photo — from your device to your hard drive and everywhere the image is published or sent.
Here’s the thing: external parties can access this EXIF data, too. And in some cases, such information could compromise the safety of your principal.
But what is EXIF data? And why is it relevant for executive protection? Let’s dive in.
What is EXIF Data?
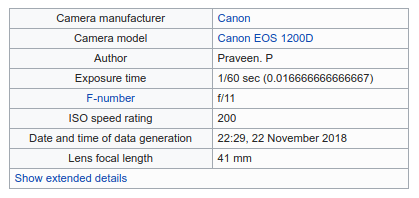
Simply put, Exchangeable Image File Format, or EXIF, is a standard for information related to an image or video captured by a camera.
This data includes settings relevant to photographers, such as ISO speed, aperture, camera model, focal length, and white balance.
Before digital cameras, photographers recorded these details by hand. Such a cumbersome process represented the only way for beginners to figure out why an image may have turned out wrong.
Not anymore.
EXIF data automates this process. That makes it easier for photographers to share information, such as tools and camera settings, that may have been used to create a particular image.
Computers also use EXIF data to organize and search through photos.
Why is EXIF Data Important for Executive Protection?
So why bring this up?
EXIF data contains a swath of personal information. And in many cases, a lot more personal information than most people know they’re sharing.
In addition to camera settings, EXIF data also records the GPS coordinates of where a photo was taken. And this information is often available to anyone that can access the image.
It’s not difficult to imagine how this could jeopardize a principal’s safety.
For instance, say a photo is taken inside an executive’s personal residence. A threat actor could use the GPS coordinates embedded in the EXIF data to determine their home address.
This isn’t a theoretical idea, either.
On numerous occasions, GPS coordinates embedded in EXIF data have compromised the safety or embarrassed individuals that failed to clear this information appropriately.
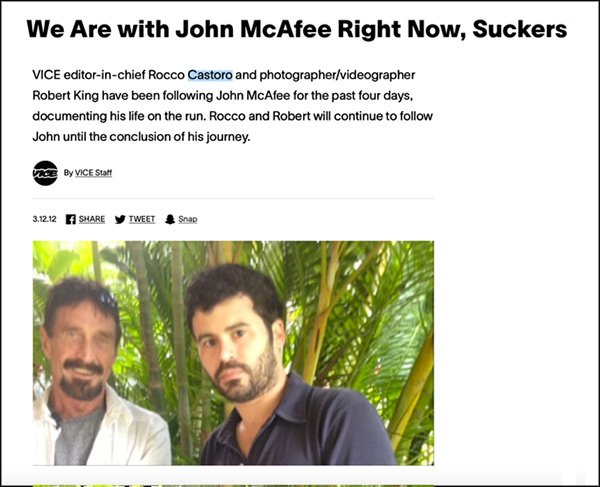
For instance, take a famous example from John McAfee. In 2012, Guatemalan authorities wanted to interrogate the tech billionaire for the murder of his neighbor. McAfee, however, claimed to have already fled the country – putting him safely out of the reach of local law enforcement.
During his escape, reporters with Vice joined McAfee’s entourage. In a snarkily titled article “We Are with John Mcafee’s Right Now, Suckers,” journalist Rocco Castoro published an image of himself with the fugitive billionaire.
Unfortunately, Vice failed to scrub the photo’s EXIF data before publication. Internet sleuths quickly learned McAfee had not in fact left Guatemala – compromising any escape plans.
Alternatively, GPS coordinates embedded in EXIF data can also provide valuable clues for analysts during an investigation.
For instance, dark web drug dealers often publish photos to promote inventory or show off the profits of their illicit activities. And while most tech-savvy criminals erase the metadata embedded in these images, some slip up from time to time.
In 2016, authorities arrested 229 dark web drug dealers after they failed to clear any EXIF data from their uploaded images. With GPS coordinates from these pictures in hand, authorities had no trouble zeroing in on their location.
How Can Protectors Safeguard Their VIPs

With regards to EXIF data, here are a few pointers protectors should keep in mind:
Where to find EXIF data
You can access some of the photo’s EXIF data by downloading an image, right-clicking on the file’s name, and clicking the “Details“ tab. Alternatively, Chrome and Firefox both have free EXIF viewer add-ons. These tools will reveal considerably more information.
How to hide EXIF Data
Professional photo editing tools, such as Lightroom and Photoshop, provide options to remove meta-data before uploading photos online.
Understand social media privacy policies
Some social platforms, such as Facebook and Twitter, scrub EXIF data from published photos to protect user privacy. Others, however, don’t follow this past practice. Be sure to understand the privacy settings of each social network your principal may use.
The Bottom Line on EXIF Data
Most people don’t understand how much personal information they might reveal about themselves through EXIF data. A shocking number of people don’t even know this information exists.
Protectors probably don’t need to put on their ‘tinfoil hats’ and begin scrubbing EXIF data from every photo posted online.
Obviously, the appropriate response depends on your threat model and the risk tolerance of your principal.
But wrapping your head around what information is publicly available on a VIP or executive represents a core function of any threat intelligence program.
And keeping this information in the back of your mind will go a long way towards keeping your principal safe.
