While no OSINT software tools can replace a solid framework and talented analysts, having the right tech stack can undoubtedly allow you to get the job done easier, better, and more efficiently.
You can find hundreds of applications out there – with prices ranging from free to thousands of dollars. They also serve different purposes, from monitoring online forums and social media to data processing and analysis. The applications and resources available for the open source intelligence community keeps growing each year.
This growth is exciting!
More tools mean that if you run into a problem, you can likely find a software solution somewhere to help you solve it. And for savvy analysts keeping up with the latest technology, more applications mean more ways to conduct creative research.
But more OSINT software can also become overwhelming. After all, how do you figure out which of the couple of hundred tools are worth buying?
This post will help clarify some of those decisions for you. Let’s look at some of the best OSINT software tools available now.
The Top OSINT Software Tools
Learn More: 5 Cognitive Biases That Could Affect Your OSINT Investigations
1. Maltego
Maltego is a data mining tool used for digital forensics and intelligence gathering. The software pulls in data about a subject from dozens of sources, then automatically displays this information in an easy-to-read graphic. That allows investigations to better understand the relationships between entities such as files, companies, websites, documents, and IP addresses.
For security teams, this can have several applications from threat modeling and incident response to vulnerability assessments. And increasingly, Maltego has become an important tool for corporate due diligence and regulatory compliance.
New users can start using the service for free with a limited number of searches. A premium version, which unlocks Maltego’s full functionality, costs extra.
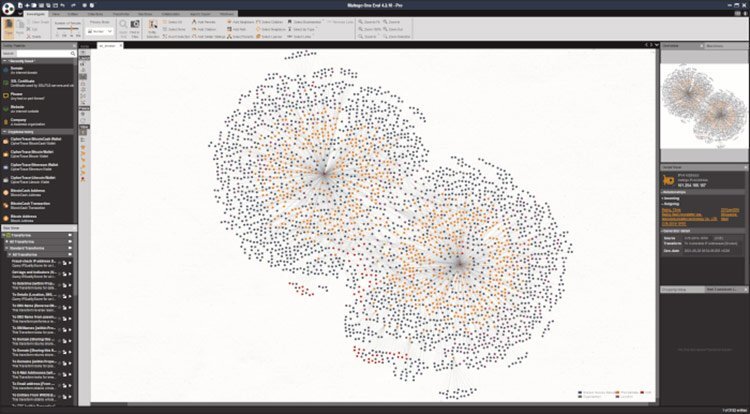 Maltego finds connections from data and displays these relationships in a handy graphical interface.
Maltego finds connections from data and displays these relationships in a handy graphical interface.
2. Exif Viewer
Each time you take a photo, your device records a swath of supplementary information about the image. These details, called EXIF data, include things like aperture, ISO speed, camera model, time of data, focal length, GPS coordinates, file names, white balance, and more.
For investigators, all of this can represent a veritable treasure trove of information. But how do you unlock this data?
Enter Exif Viewer. This OSINT software tool allows you to extract and view EXIF data from online photos.
Analysts can exploit this information in several ways. For instance, odd file names can sometimes tip off investigators that an image is fake. GPS coordinates embedded in images could reveal the location of a person of interest.
Additionally, the app allows users to publish images without accompanying EXIF data. For security teams or close protection details, this is a good habit. Masking EXIF data prevents others from determining where and when an image was taken – which can potentially jeopardize the safety of a client.
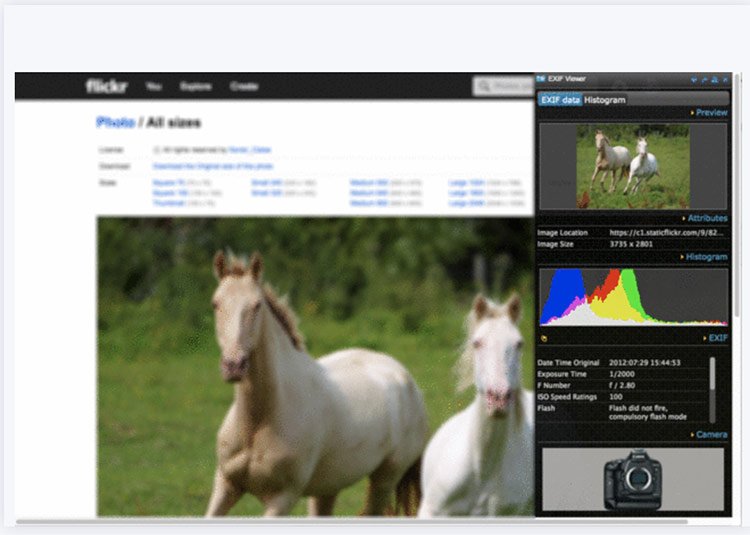 OSINT analysts can use the Exif Viewer app to uncover metadata embedded in an image.\
OSINT analysts can use the Exif Viewer app to uncover metadata embedded in an image.\
3. Navigator
Users upload terabytes of content to the web every minute. This information can have enormous intelligence value for security teams. But no organization has the resources to manually shift through and analyze all of this data. And as a result, it’s easy to overlook critical threats to your people, assets, and operations.
Enter Navigator.

Navigator allows your security teams to monitor the web 24/7 to detect high-risk threats. Simply create a query based on a series of relevant keywords. When Navigator detects that phrase published somewhere online, it sends out an automatic alert to your email or mobile device.
For a resource-strapped security detail, this can be a big time-saver. No longer do analysts have to spend hours manually monitoring the web and social media. Once they have set up an automated query, they can free up hours for more important tasks. And by casting a wide net for data collection, they’re far less likely to miss a serious threat.
4. SpiderFoot
SpiderFoot is an OSINT reconnaissance platform that can help automate routine searches and queries. To start, enter the subject you want to investigate. The OSINT software tool will then collect data from over 100 public sources to provide a complete picture of your target entity.
This can have several applications for security analysts from red team exercises and penetration testing or gathering threat intelligence. Data returned from SpiderFoot can also reveal possible data leaks or other system vulnerabilities in network infrastructure.
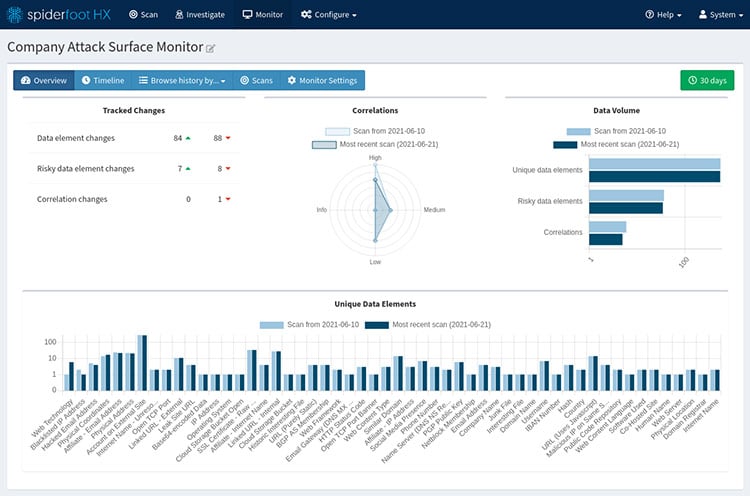 SpiderFoot can help automate routine searches and queries.
SpiderFoot can help automate routine searches and queries.
5. Dehashed
Over 2.0 billion records containing usernames and passwords were compromised in 2021, according to a recent report by ForgeRock. Worse still, that figure continues to grow year after year.
For that reason, we can say with confidence that someone in your organization has been (or will soon be) the victim of a data leak. And that can represent a serious vulnerability for businesses and individuals. So how can security teams address this problem?
Enter DeHashed. Created for journalists and cybersecurity professionals, DeHashed is a search engine for uncovering hacked databases and records. The service allows users to scan the web for compromised information, such as names, email addresses, phone numbers, URLs, IP addresses, etc.
Users can perform a basic search for free after creating an account. Detailed searches and automated monitoring services, however, require a paid subscription.
 DeHashed is a search engine for uncovering hacked databases and records.
DeHashed is a search engine for uncovering hacked databases and records.
6. Shodan
Nowadays, websites aren’t the only thing connected to the internet. Billions of physical devices, from light bulbs and webcams to surveillance cameras and industrial control systems, are now hosted on the web. But is it possible to exploit these devices for intelligence-gathering purposes?
Let me introduce you to Shodan. Short for the Sentient Hyper-Optimized Data Access Network, this search engine maps and collects information from millions of internet-connected devices and systems worldwide.
Such a set-up makes network monitoring a breeze. Cybersecurity teams can exploit Shodan’s functionality to monitor devices and servers within their network that have direct internet access — and are hence exposed to attacks. Other applications for the search engine include market research, vulnerability analysis, and penetration testing.
 Analysts can use Shodan to monitor devices and servers within their network that have direct access to the internet — and are hence vulnerable to attack.
Analysts can use Shodan to monitor devices and servers within their network that have direct access to the internet — and are hence vulnerable to attack.
7. Obsidian
Obsidian is the smart-note app taking the OSINT community by storm. And while developers may have created the tool with academics in mind, its capabilities have found a growing fan base among threat analysts and researchers.
Like similar apps, Obsidian allows you to record and display notes. But its real power comes from the app’s backlink feature. Obsidian allows users to create links between disparate files, turning a collection of plain text notes into a rich network of linked thought. And a handy graphical interface makes it easy to perform a link analysis between different groups and entities.
You can download a free version of the program with limited features for personal use. A commercial license starts at $50.00 per month for each user.
 Obsidian allows users to create links between disparate notes, turning a collection of plain text files into a rich network of linked thought.
Obsidian allows users to create links between disparate notes, turning a collection of plain text files into a rich network of linked thought.
OSINT Software Tools: The Bottom Line
We know that searching the web for the right investigative programs can feel daunting. There are just so many options out there. So, we’ve done the leg work for you in this list of go-to OSINT software tools.
Of course, all the OSINT software tools in the world won’t make you a great analyst. But they can help you automate many routine processes – resulting in a faster and more efficient investigation.

