Open Source Intelligence (OSINT) has experienced tremendous growth during the past years; transitioning from an expendable part of the intelligence world—to a foundational tool.
With the advent of the internet and social media, users upload terabytes of content to the web every minute. That represents enormous intelligence value for anyone that can sift through and analyze all of this information.
Whether safeguarding executives, preventing violence and disruption, or responding faster to emergencies, security professionals have started to recognize the value OSINT can have in their day-to-day operations.
But if you’re new to the field, where do you even get started?
In this OSINT for beginners guide, we’ll answer that question along with some others like what open source intelligence is, how OSINT supports enterprise security, and where to get started when conducting your own OSINT investigations.
Let’s dive in.
JUMP TO SECTION:
OSINT for Beginners: What is Open Source Intelligence?
Open source intelligence, or OSINT, refers to any information collected from free, public sources about an organization or individual to provide actionable insights for decision-makers.
Technically, this information could be from any public data source, such as books, magazines, and newspapers. In practice, analysts nowadays conduct most of their tradecraft online.
The origins of the field can be traced back to World War Two. In 1941, the Office of Strategic Services, a precursor to the CIA, assembled a branch of researchers dedicated to gathering information from public sources. They collected materials from around the world and combed through this information for any intelligence on enemy activities.
Today, a wide variety of individuals and organizations apply open source intelligence. Academics and journalists, for instance, use OSINT to conduct research. Law enforcement and private investigators rely on OSINT to solve cases. Militaries exploit OSINT for strategic planning and organizing combat operations.
In the private sector, security teams use OSINT to safeguard customers, employees, and property. And it's not uncommon for organizations to assemble intelligence teams to conduct due diligence on new hires, business partners, or acquisition targets.
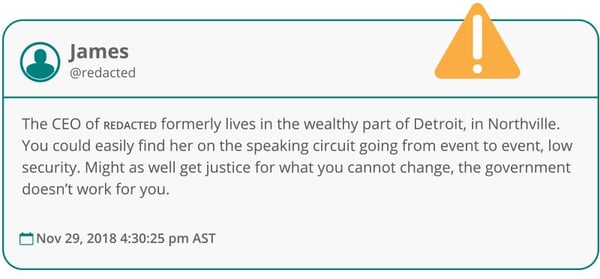 A threatening post directed towards a senior executive of a Fortune 500 company, discovered by Navigator. Identifying information has been redacted.
A threatening post directed towards a senior executive of a Fortune 500 company, discovered by Navigator. Identifying information has been redacted.
But while organizations use OSINT to watch threat actors, threat actors also use OSINT to watch organizations. To plan attacks on targets, criminals exploit open source intelligence techniques to find weaknesses in corporate infrastructure. Alternatively, hostile nation-states may use OSINT tools and tactics for similar purposes.
|
Case Study: |
Learn More: 5 Cognitive Biases That Could Affect Your OSINT Investigations
Benefits of OSINT for Physical Security
Most businesses take a “guard at the gate” approach to security. In other words, they wait for something to go wrong and respond appropriately.
But such a reactive approach falls short. Firstly, organizations that don’t proactively assess their vulnerabilities have a higher likelihood of being impacted by a security incident in the future. Moreover, it can be more expensive to respond to an incident after it occurs than to prevent one altogether.
But taking a more proactive stance, by using information collected from open sources, has several benefits for physical security teams such as:
- Improve resource allocation. Security leaders can use OSINT to quantify risks in monetary terms. That represents valuable information when allocating scarce resources or justifying an investment in security programs to executives and board members.
- Mitigate risk. Security leaders can use OSINT to assess their organization’s vulnerabilities and develop mitigation strategies. Advance warnings from open source intelligence can often allow security teams to prevent incidents before they even occur.
- Reduce response times. OSINT can alert security teams to incidents almost as soon as they happen. Not only does this mean saving precious minutes or hours when they count the most. Intelligence gathered from open sources can also result in better decisions during the heat of the moment.
- Cut costs. Ultimately, the benefits of OSINT trickle down right to the bottom line. Mitigating and responding faster to incidents means less business downtime, fewer fines from regulators, and smaller losses in the way of theft or fraud. And while security teams may have trouble quantifying other benefits, they are no less important.
- Cheaper capital. If you can manage risks better than your peers, then your business will have more predictable earnings. Over time, shareholders and lenders reward this predictability with a lower risk premium on capital. Depending on the size of the business and its cost of funding, this enhanced predictability can translate into hundreds of millions of dollars in added market value for the company.
And these upsides go far beyond the safety of people and property.
Conducting OSINT can benefit a swath of departments in the organization, from marketing and human resources to logistics and procurement. And by enabling operations where others fear to tread, organizations applying these tools and techniques can develop a competitive advantage over rivals that don’t have any OSINT capabilities.
Of course, open source intelligence doesn’t represent some silver bullet for security programs. By definition, OSINT can only uncover threats that appear in the public domain. So analysts will have a tough time detecting malicious individuals that conceal their activities. And open source intelligence will never be able to replace all aspects of a well-structured security program.
That said, OSINT can represent an enormous force multiplier in most businesses. And that can go a long way toward keeping customers, employees, and property safe.
|
Case Study: Microsoft’s in-house intelligence team, however, managed to provide a more nuanced assessment tailored to the company’s footprint. They determined executives would face few security risks in the areas near corporate offices. That gave the C-suite the confidence they needed to continue operating in the area safely. |
How is OSINT Used for Enterprise Security?
Security leaders have realized it is far cheaper to gather intelligence upfront and address problems proactively than to get caught flat footed responding to an unexpected incident.
Still, many organizations fail to exploit OSINT to its full potential. And this usually happens because managers and directors have not considered a potential use case until after an incident occurs.
So how can organizations unlock the power of open source intelligence for enterprise security? To answer this question, it’s often helpful to see how other firms exploit OSINT in their day-to-day operations.
Let’s look at some examples:
- Executive Protection. OSINT has become an essential tool for protectors when safeguarding VIPs. While on the road, for instance, security details can scan open sources to conduct regional risk assessments, identify possible risks, and set up alternative travel plans. Additionally, high-profile individuals often find themselves subject to violent threats online. OSINT tools allow details to detect threatening posts, validate the threat, and plan an appropriate response.
- Crisis Response. People often report events on social media hours or even days before events get picked up by news outlets. By continuously watching these channels, security teams can be alerted to a crisis almost as soon as they happen. Furthermore, commentary gathered through open sources, such as photos, audio, and comments, can allow analysts to respond more effectively.
- IP Protection. Advanced OSINT software can reveal criminal networks on the web engaging in counterfeiting, content piracy, and illegal streaming. Security teams also use open source intelligence techniques to identify malicious insiders selling closely-held company secrets online, such as patents, research plans, or product roadmaps.
- Brand Protection. Unsanctioned activities under your organization’s logo can damage your firm’s reputation (i.e. executive impersonations, typosquatting websites, or employment scams). That could also include criminal activities on company property, such as human trafficking. Open source intelligence, however, allows organizations to identify and address these issues.
- Data Leak Detection. Accidental data leaks by employees and other stakeholders represent an underrated threat to organizations. For instance, an employee may publish a picture of their work badge on social media. Malicious individuals can exploit such information to create fake credentials and gain unauthorized access to company facilities. But by monitoring open channels, analysts can spot and address these breaches before any problems occur.
- Supply Chain Protection. Supply chain havoc can result in missed deadlines for product deliveries. Avoiding such problems requires having all available information on hand concerning emerging and current threats. Sure, new technologies such as IoT sensors and the blockchain play a role in this process. But OSINT provides decision-makers with the context they need to adapt effectively in a crisis.
- Event Security. Many issues could disrupt an event: trespassers, rowdy fans, poor weather. Thankfully, threat intelligence from online chatter can allow you to spot potential problems ahead of time. With that information on hand, security teams can work to mitigate risks, respond faster to incidents, and deploy resources more effectively.
- Cybersecurity. Intelligence allows tech teams to identify and fix vulnerabilities in network systems. That can put organizations in the position to respond faster to breaches that have already happened. Or even better, they may be able to stop cyberattacks before they even occur.
- Risk Analysis. OSINT can capture on-the-ground “chatter,” providing insights into the mindset and opinions of locals in a region. That could represent invaluable information for decision-makers when considering a new project or expanding into another territory.
- Fraud and Loss Prevention. Anti-fraud and loss prevention teams need up-to-date details on the latest theft techniques. Surprisingly, criminals often boast about their exploits online. This information empowers organizations to better safeguard their operations from theft and fraud.
- Due Diligence: Doing business with money launderers, tax evaders, or other criminals can hurt your organization's reputation. And because of growing fines from regulators, decision-makers have invested more effort into due diligence. When entering new markets or bringing on a new customer, intelligence teams can help executives avoid doing business with dodgy partners and assess potential conflicts of interest.
|
Case Study: In the following days, the intelligence team advised management to purchase protective equipment for personnel such as masks and hand sanitizer. Security even started preparations for moving employees to an online work setup. That resulted in a smooth transition to a remote office when the virus reached the United States. |
Read more:
- 7 Ways to Use OSINT for Corporate Security
- 5 Ways OSINT Supports Oil and Gas Security
- What Businesses Need to Know About OSINT for Physical Security
- Monitoring an Outbreak with OSINT
- How Does OSINT Support Close Protection Teams
- How to Use OSINT to Detect Data Leaks and Breaches
BACK TO TOP >
How is OSINT Collected?
Generally speaking, analysts have two methods of gathering information: passive and active.
Passive collection refers to the quiet observation of data generated by a target. That could include techniques such as studying maps, performing Google searches, reading news reports, reviewing public records, or scanning social media.
Anonymity represents the main advantage of a passive approach. Provided you practice good operational security, such as using a VPN, the Tor browser, or a virtual machine, you have little risk of being detected by targets. And most passive collections can be done remotely.
On the other hand, passive OSINT may not always be reliable or as detailed as other investigative methods. That can mean spending a lot of time processing and analyzing information after collection.
On the other end of the spectrum, active collection refers to when a researcher comes into contact with the target. That could include infiltrating an online forum by setting up an account or scanning a network system for vulnerabilities. Active collection could even involve real-world interactions, such as dumpster diving, talking to friends and associates, or visiting a target’s physical location.
Detection, however, presents the biggest risk with this method. Active collection puts you in close contact with the subject. If detected, a target may destroy evidence or take retaliatory measures against you and your organization.
Additionally, active research tends to be narrow in scope. By definition, it’s resource-intensive and tough to scale. So security teams relying too heavily on this method could miss out on other threats.
That said, active collection can be highly accurate. And more often than not, this method can deliver insights that would be impossible to obtain otherwise. But generally speaking, most OSINT techniques fall under the passive category.
That said, analysts even have a third option, dubbed semi-passive collection, which falls between the previous two. This approach involves using the active collection measures of a third-party service to perform passive analysis.
Types of OSINT Data Sources |
|
|
|
To illustrate these different approaches in action, let’s say we both work for a large hedge fund.
Before investing in a particular stock, we would want to conduct due diligence on the business. That will probably require learning more about the firm's sales prospects, potential risks, executive team, and future business plans.
We could employ active intelligence gathering techniques, such as visiting the corporate headquarters or asking questions to management directly. But for obvious reasons, any responses would likely be positive and self-serving.
Worse, poking around the company campus could tip outsiders off that we want to buy a stake in the business. That could send the stock price soaring before we can build our stake.
Instead, we could use open source intelligence to gather clues about the company.
To evaluate management's credibility, for instance, we could review legal filings and media reports. One could get some idea of future sales prospects by reading customer reviews online or Google search trends. It might even be possible to guess the firm's next acquisition target by following the flight records of the CEO’s private jet.
|
OSINT for Beginners Tip: That can create a problem for intelligence teams. In recent years, millions of users have migrated to alt-tech websites like Gab, 4Chan, Telegram, and Rumble. So if you’re not monitoring these platforms, you could overlook serious threats to your organization. You can learn more about them by clicking here. |
Read More:
- 5 Tips for Conducting OSINT on Alt-Tech Social Networks
- 6 Tips for Gathering OSINT on TikTok
- How to Collect OSINT on the Dark Web
- How to Conduct OSINT on Telegram
BACK TO TOP >
The OSINT Intelligence Cycle
Over the past few years, collecting and processing open-sourced data has become more complex.
Practitioners have to comb through more sources than ever before. Various groups, from state-backed actors to conspiracy theorists, have flooded the web with mis- and disinformation. All of which has made collecting data a more tedious and time-consuming process.
In response, analysts rely on a structured system to produce actionable insights for clients, often dubbed the ‘OSINT Intelligence Cycle.’
Different organizations may conceptualize this process differently. Typically, though, it is broken down into between four and seven steps. But the end result is the same.
Here’s a quick breakdown:
- Planning and Direction: The intelligence cycle typically begins with a request from a decision-maker. Such a request could be through formal channels or something more informal like a phone call or email. Regardless, this phase requires outlining the priorities and deliverables for the project. Analysts should also define what type of data they will need, how they will find these sources, and what they hope to accomplish with this information. Ironing out these details before diving into research should ensure an efficient and productive operation throughout the remaining phases of the intelligence cycle.
- Collection: After the intelligence team has defined their objective and operational plan, they can begin collecting data. Technically, OSINT refers to any materials available freely to the public, such as books, libraries, or magazines. In practice, however, analysts typically collect most of their data online. Teams can complete this work manually. Alternatively, well-staffed, well-funded organizations may employ tools to automate this process.
- Processing: Processing refers to organizing and indexing raw data into something more useful for investigators. Analysts apply screens to text data, filtering out irrelevant information and converting what's left into a usable format for other data feeds and tools. These efforts ensure they can locate and review raw data discovered during the collection phase later.
- Analysis: Once analysts have collected and processed their raw data, they move on to the analysis phase. Here researchers review information to identify trends, patterns, or inconsistencies. During this step, the team will draw conclusions and provide recommendations for decision-makers.
- Dissemination: During the dissemination phase, OSINT analysts decide how they will communicate their findings to stakeholders. They can accomplish this through several methods, such as an email, presentation, memo, report, or phone call. Regardless, analysts must consider the preferences of the decision-maker.
- Feedback: Once an analyst disseminates an intelligence product, they receive feedback from the end customer or decision-maker. This feedback determines whether the product produced satisfied the initial goals of the investigation and whether the intelligence cycle should start again. The team may also use this step to adjust and optimize their processes for future assignments.
|
Case Study: OSINT investigators at a media group called Bellingcat, however, remained skeptical. By digging into the metadata of the video, they discovered it had been filmed weeks before the attacks purportedly happened. More incredibly, sounds of explosions and gunfire also appeared to be directly copied from a clip of a Finnish military training exercise published on YouTube years earlier. This evidence allowed the team at Bellingcat to conclude that some agency had likely fabricated the video. |
Identifiers and Pivots
Now that we have reviewed what open source intelligence is and how it benefits organizations, let’s review two foundational concepts of OSINT for beginners: identifiers and pivots.
Identifiers are unique characteristics that describe an object, property, or individual. For example, possible identifiers include names, addresses, pictures, or website URLs. Any one identifier could exist across multiple datasets in any number of places across the internet. But on their own, a single identifier doesn’t tell you very much.
Types of Identifiers |
|
|
|
To extract more information on a subject, experienced OSINT analysts use a technique called "pivoting." Simply put, pivoting means searching for the same identifier in a variety of datasets to uncover new identifiers on a target. And it's this ability that represents the real hallmark of a great OSINT investigator.
For example, you may start an investigation with only an anonymous blog post. Searching through WhoIs domain registries, you may be able to find a name and email address. A quick Google search might uncover photos, close contacts, and social media accounts.
So in this case, you could say you’ve pivoted from a website URL to a name, email address, and other information. With more digging, you may be able to create a full profile on your subject.
|
OSINT for Beginners Tip: |
10 OSINT Tools Every Analyst Should Bookmark
Users upload terabytes of content to the web each day – far more information than any individual could shift through in a lifetime. And the complex ways threat actors conduct their activities online have also left organizations more vulnerable.
For those reasons, analysts increasingly rely on automated OSINT tools to help them with their job. While no software can replace a talented analyst with a good framework, having the right instruments at your disposal can help you deliver intelligence faster, better, and more efficiently.
Below, we’ve highlighted a handful of free and paid applications every investigator should bookmark. To be clear, the tools mentioned here do not represent a comprehensive list. But it does serve as a great place to get started.
1. The Wayback Machine
Artifacts published on the web can disappear at any time. For that reason, experienced OSINT analysts always record information collected during an investigation. It might not be there again the next time you reload a website.
But if you want to review content that someone has already removed, this isn't an option. Thankfully, that’s where The Wayback Machine can come to the rescue.
The Wayback Machine represents the world's largest digital archive. The site crawls through millions of websites each day, taking screenshots to preserve some aspect of internet history. And it comes in handy when you want to review content on a page that users have since removed.
Best of all, the Wayback Machine is free and easy to use. First, enter the URL of the site you want to research. Then choose a date and timestamp from the timeline. You will then see a screenshot of that page as it looked at that moment.
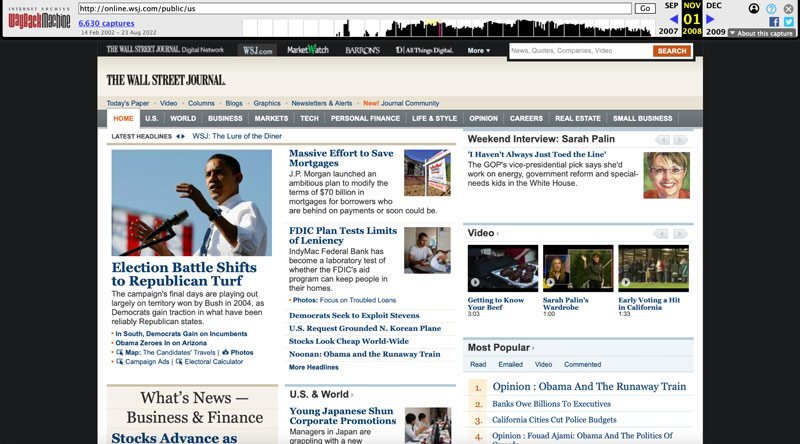 The homepage of the Wall Street Journal on November 1, 2008, captured by the Wayback Machine.
The homepage of the Wall Street Journal on November 1, 2008, captured by the Wayback Machine.
2. Exif Viewer
People have always said a picture is worth a thousand words. Today, they mean that quite literally.
Every time you snap a photo, your device records a swath of supplementary information about the image, called EXIF data. These details include facts like ISO speed, aperture, camera model, focal length, white balance, and more. All of which can have enormous value for OSINT investigators.
One of our favorite OSINT software tools for uncovering this information: Exif Viewer. This Chrome app allows you to view EXIF data from online photos. That usually includes file names, the type of camera used, the time and date the image was taken, as well as any embedded GPS coordinates.
OSINT analysts can exploit this information in several ways. For instance, GPS coordinates embedded in an image could give away the location of a subject. Alternatively, EXIF data could reveal whether an image posted online is genuine or fake.
 OSINT analysts can use the Exif Viewer app to uncover metadata embedded in an image.
OSINT analysts can use the Exif Viewer app to uncover metadata embedded in an image.
3. Fake Name Generator
For many reasons, analysts usually don’t want to reveal their identities online. So to interact with others, many investigators create sock puppet accounts – fictitious personas created to conduct research anonymously.
But building a believable, fully-developed pseudonym can take a lot of time – which becomes an especially big headache if you need to create multiple aliases. Enter Fake Name Generator.
This free application produces an entirely new identity for a person. That includes a swath of personal details, such as age, height, weight, contact information, street address, credit card numbers, phone numbers, favorite colors, and more.
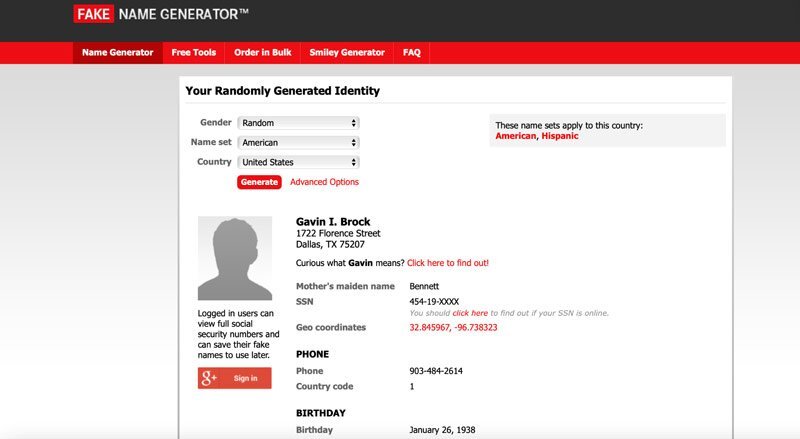 Fake Name Generator produces an entire fake persona for an alias or sock puppet account.
Fake Name Generator produces an entire fake persona for an alias or sock puppet account.
4. Live UA Map
Need a snapshot of what’s happening on the ground in a given area? Then you’ll want to check out Live UA Map.
This application plots breaking news reports from social media on a map interface. That makes it easy for users to find relevant stories at a glance. You can also use the archive feature to review events reported days or weeks ago, providing a sense of risks and trends in a given region.
Useful for analysts trying to predict future conflicts, emergency response teams looking for timely alerts on natural disasters, or corporate security teams assisting VIPs and executives while traveling.
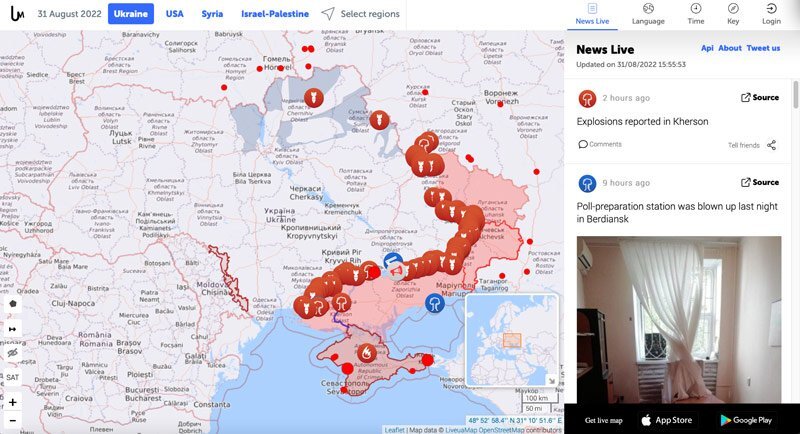
Analysts can use Live UA Map to track events in conflict zones.
4. Navigator
Since we live and breathe OSINT here at LifeRaft, we hope you don’t mind if we add our own Navigator software to the list.
Navigator allows users to set up customized screens to monitor the web for high-risk threats to their organization. In addition to the largest social media platforms, the software scans more obscure online communities such as forums, paste sites, chan boards, and the dark web. When the platform detects a threatening post, users receive an automated alert to their email inbox or mobile device.
That can represent a big force multiplier for a resource-strapped security team. Manually monitoring and collecting data from social media is time-consuming. But by automating this process through Navigator, investigators can spend more time analyzing information and advising decision-makers.
 Navigator allows users to set up customized screens to monitor the web for high-risk threats to their organization.
Navigator allows users to set up customized screens to monitor the web for high-risk threats to their organization.
5. Shodan
Websites aren’t the only thing hosted on the internet. Today, billions of physical devices, such as smart homes, surveillance cameras, and industrial control systems, are now connected to the web.
Shodan, short for Sentient Hyper-Optimized Data Access Network, is a search engine designed to map and collect information about these internet-connected devices and systems.
That can have several applications for OSINT researchers, especially those in cybersecurity. Analysts can use Shodan to monitor devices and servers within their network that have direct internet access — and are hence vulnerable to attack. Applications for the search engine include vulnerability analysis, penetration testing, and market research.
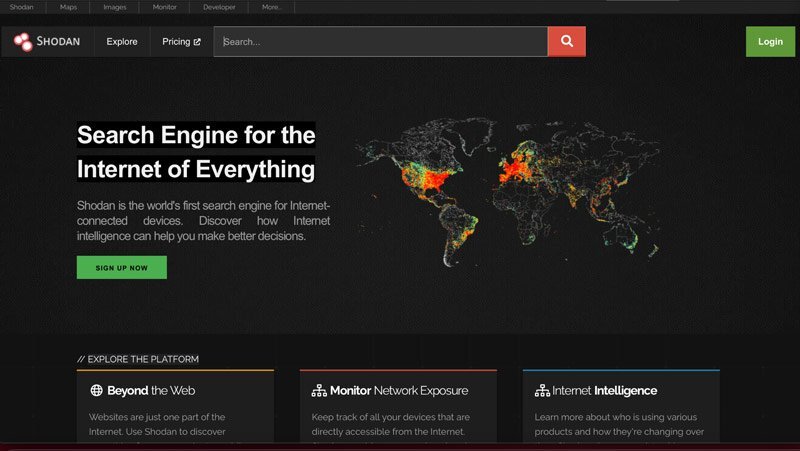 Analysts can use Shodan to monitor devices and servers within their network that have direct access to the internet — and are hence vulnerable to attack.
Analysts can use Shodan to monitor devices and servers within their network that have direct access to the internet — and are hence vulnerable to attack.
6. Maltego
Maltego ranks as one of the more popular tools within the OSINT community. Users feed the software some sort of identifier that they want to investigate further, such as a URL, email address, IP address, or domain name. Maltego then finds connections from the data and displays these relationships inside an easy-to-read graphical interface.
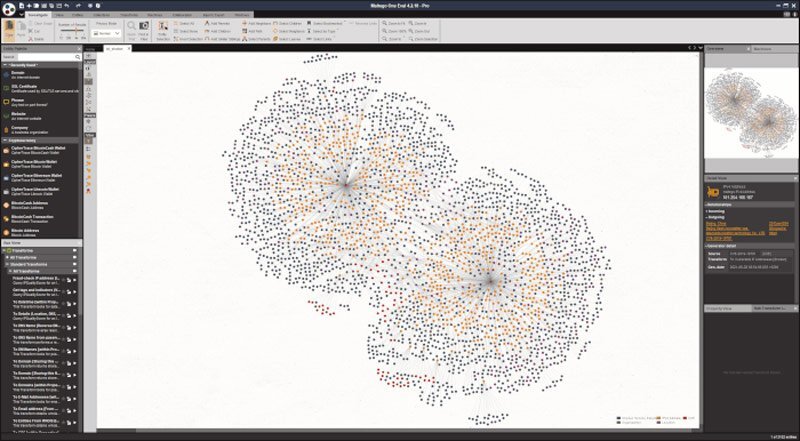
Maltego finds connections from data and displays these relationships in a handy graphical interface.
7. TinEye
When you stumble across an image during an investigation, you might want to determine whether others have published this photo elsewhere.
Analysts do this through a technique called reverse image searching. By finding other places that contain the image, you can gain more relevant information that might be useful in your research.
One of our favorite OSINT tools for reverse image searches: TinEye.
To use the application, upload your image. TinEye then uses advanced pattern recognition and machine learning algorithms to retrieve information on the picture, such as use, original origins, and higher resolution versions.
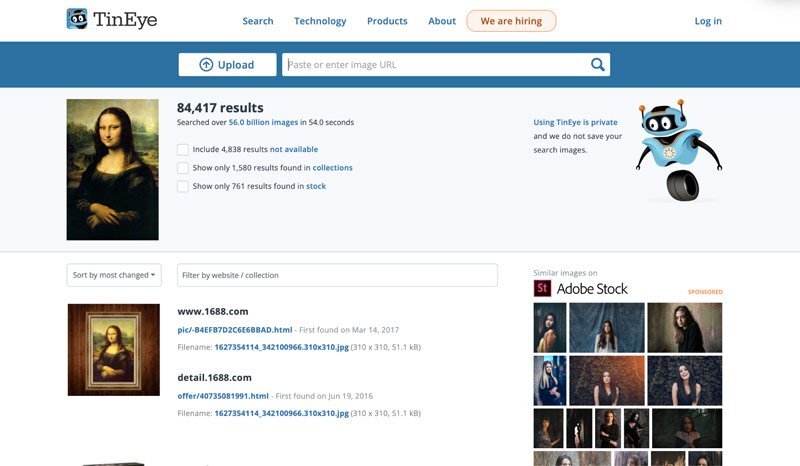
TinEye then uses advanced pattern recognition and machine learning algorithms to determine the original origins of images published online.
8. Haveibeenpwned
Email data leaks can present a serious security risk to organizations.
For starters, hackers can exploit leaked credentials to compromise accounts. Breached data sets often include a swath of personal information, which threat actors can weaponize to harm a VIP or principal.
And given disclosed breaches exposed over 21 billion records last year alone, we can say with confidence that someone in your organization has been (or will soon be) a victim in one of these incidents.
Haveibeenpwned represents one useful OSINT tool to mitigate this threat. This site doesn’t contain links to any breached data itself. Instead, this tool allows users to check if any of their accounts have been compromised in a recent leak.
To use the application, type your email address or phone number in the search bar on the home page and click Enter. The site will then scan through its database and alert you if your credentials have been found in any breaches.
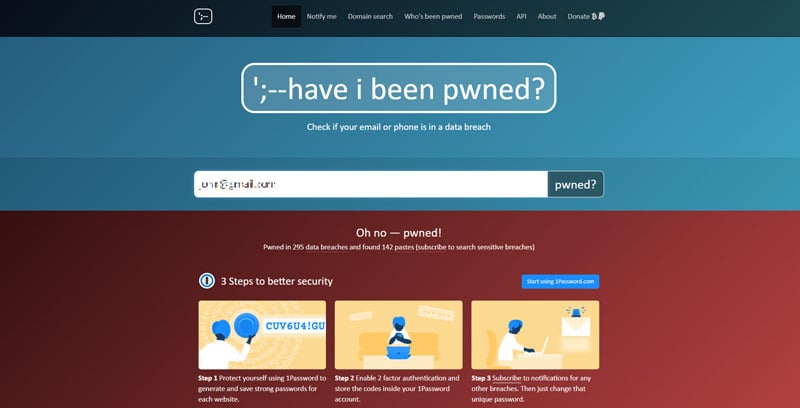
Haveibeenpwned is a free service that allows investigators to determine whether an email address has been compromised in a previous data breach.
9. Ahmia.fi
The dark web refers to encrypted online content not indexed by regular search engines.
Created by the U.S. Navy in 2002, the dark web first served as a way for agents to avoid detection while navigating the internet. But to prevent operations from standing out like a sore thumb, the military opened the service up to the public. And today, the dark web allows anyone to communicate online with more anonymity.
Such anonymity, as you might expect, has attracted a swath of dodgy characters. Dark web forums serve as hubs for criminal markets, with vendors peddling everything from drugs and pirated content to illegal pornography and stolen credit card numbers. But this corner of the web also serves as a tool for journalists, whistleblowers, and activists.
One way to find content on the dark web: Ahmia.fi. To use this free application, type a search term into the query box and click enter. The search engine will then return any relevant onion addresses it has indexed.
Because the dark web is tricky to navigate, Ahmia won’t deliver reliable results like a normal search engine such as Google. Still, it’s a useful service.
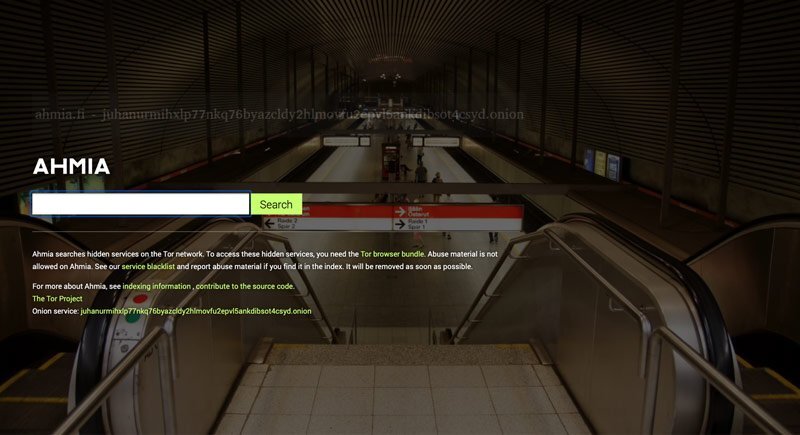 Ahmia.fi is a free service that allows users to search for dark web content.
Ahmia.fi is a free service that allows users to search for dark web content.
10. Whois.com
The WhoIs system can represent a proverbial goldmine for OSINT investigators. In the same way homeowners must register their house with a governing agency, website owners must register their domain names with relevant contact information.
That often includes valuable intelligence on those running the site, such as an address, email, and phone number – all of which could be useful when conducting due diligence on an organization.
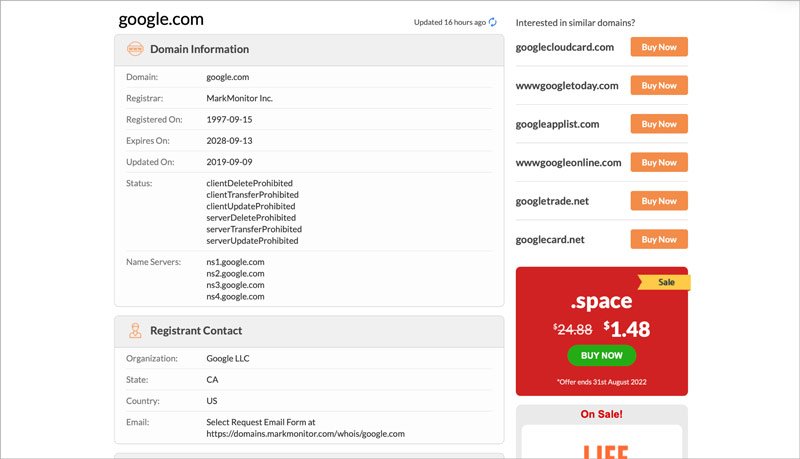 A WhoIs domain lookup can provide a vast amount of information behind the owners of a website, including names, emails, addresses, and phone numbers.
A WhoIs domain lookup can provide a vast amount of information behind the owners of a website, including names, emails, addresses, and phone numbers.
As mentioned, the resources highlighted above do not represent a comprehensive list of OSINT tools for researchers. Depending on the requirements of your investigation, you will likely need to find or develop your own alternative applications. And the list of resources you keep bookmarked as an analyst will naturally grow over time.
Still, the programs above serve as a good place to get started.
|
OSINT for Beginners Tip: |
Read More:
- 7 OSINT Websites Every Analyst Should Bookmark
- The 7 Best OSINT Tools for Social Media
- How to Use OSINT Tools for Executive Protection
- 9 Ways to Use OSINT Tools for Sports Security
- Open Source Intelligence Platform Evaluation: 7 Points to Consider
BACK TO TOP >
What New Analysts Need to Know About Operational Security
OSINT tools allow you to watch bad actors online. But never forget bad actors can use these same OSINT tools to watch you.
Because you can conduct open source research from the comfort of your home or office, it’s easy to develop a false sense of security. Especially when compared to other forms of intelligence gathering, such as interrogations and surveillance in the field, OSINT can feel downright pedestrian — hardly the stuff of a great James Bond movie. But new analysts must remember that any open source research comes with certain risks.
Cybersecurity, for starters, represents one obvious concern. Analysts conduct a great deal of OSINT research on some of the doggier corners of the internet. This exposes them to many web-borne threats such as viruses, trojans, worms, and other types of malware. If you fail to protect your work terminal, any web code executed locally could compromise your machine and your organization’s network.
Detection presents another problem. Individuals conducting malicious activities online generally don’t want to be found out. If they realize they’re under surveillance, they could begin covering their tracks by deleting evidence – potentially compromising your investigation. Even worse, some bad actors might seek retribution against you and your organization.
For these reasons, open source investigators must practice good operational security or OPSEC. In 2022, UC Berkeley published “The Berkeley Protocol on Digital Open Source Investigations.” This document provided a framework for how OSINT analysts can safely operate online. And while the authors published this guide for research on international human rights violations, it still has many good recommendations for analysts in other fields.
For example:
- Assume you’re always under surveillance: OSINT researchers should start with the assumption that unwanted third parties monitor their activities at all times. Conduct all operations in a way that is consistent with your online persona to avoid revealing any identifying details.
- Never mix professional with personal activities: For convenience, it can be tempting to use a personal device for investigative purposes. This practice, however, can result in cross-contamination between your personal information and your online investigative persona. That's why investigators should always use distinct hardware and software to avoid mixing their personal and professional activities.
- Disguise your attribution details to third parties: Every time you visit a website, you reveal information to third parties, such as your IP address, operating system, timezone, language, keyboard settings, and other details. These tidbits, once snitched together, could potentially reveal your identity to others. For this reason, investigators should take steps to avoid leaking identifying details when online. Basic actions include using a secure-focused browser and connecting to the web through a trusted VPN. Managed attribution services, such as our friends at Authentic8, even allow you to customize your online appearance to others. That makes it easier to blend in with internet traffic.
- Secure environments: OSINT investigators should employ technical systems that limit exposure to cyber threats such as viruses or other malware. A virtual machine, for instance, uses separate CPU, RAM, and storage on your workstation. That creates a sandboxed environment to conduct your work, protecting your system from web-borne threats. For extra protection, some analysts recommend investing in an isolation service, which allows you to browse the web from a cloud-based server.
- Browser security: Analysts conduct most of their online investigations through a browser of some type. Yet this tool represents a common and often overlooked security vulnerability. Browsers are susceptible to a wide variety of cyber threats, for starters. And tracking methods, such as cookies, can reveal identifying information to third parties. To stay secure, many OSINT analysts recommend using a privacy-focused browser, such as Brave or Tor, with javascript disabled.
Designing effective OPSEC procedures is not a one size fits all policy. The specific methods you employ will depend on a threat assessment of your targets as well as the risk tolerance of your organization.
For instance, say your company uses open source intelligence for early alerting on natural disasters near corporate facilities. That will require far more relaxed procedures than investigating credit card fraudsters on the dark web.
Regardless of your mission, however, OSINT researchers must have a plan before conducting any investigation. That means understanding the digital environment while using the right tools to stay safe. And taking these measures upfront will go a long way toward ensuring the ongoing success of your operations.
|
OSINT for Beginners Tip: Incognito Mode, for instance, blocks some tracking services from watching you while you’re on the web. Yet search engines still have other ways to monitor your activities, like e-tags and supercookies. Moreover, a VPN may disguise your location to third parties. But these services can still leak information about your device, such as timezone, keyboard settings, and operating system. |
A full breakdown of operational security for OSINT investigations goes beyond the scope of this article. So if you’re interested in learning more about this topic, be sure to check out the resources below.
Read more:
- Basic OpSec for the Uninitiated
- Basic OPSEC Tips & Tricks for OSINT researchers
- What VPNs and Incognito Mode still give away in your online identity
- OSINT OPSEC: The Mistakes Most Analysts Make
BACK TO TOP >
How OSINT Impacts Mental Health: 9 Ways to Protect Yourself
Staying safe online means more than just using a VPN.
At LifeRaft, we know from talking to hundreds of OSINT analysts that repeated viewings of graphic imagery can impact our mental health. And this represents an often underrated workplace hazard in our profession.
Yes, the intelligence community plays a key role in keeping clients, employees, and customers safe. But such work often requires repeated exposure to extremist content and violent imagery – all of which can lead to secondary trauma.
So how can we address this issue? In a recent LifeRaft webinar, Mike Evans, Head of Intelligence for Securitas SIU, provided nine tips analysts can use to reduce the impact of upsetting content:
- View violent or graphic content in a well-lit room with colleagues nearby.
- Learn how to spot the signs of vicarious trauma.
- View graphic imagery in black-and-white with the audio at a low volume on a smaller screen.
- Avoid taking your work home with you if possible.
- Have a plan for how you will collect and process upsetting material.
- Take multiple breaks during sessions where possible.
- Schedule a specific time to review graphic content with strict time limits.
- Check in frequently with colleagues and team members.
- If available, consider using mental health support programs offered by your organization.
Read more:
- Vicarious trauma and OSINT – a practical guide
- How to Prevent, Identify and Address Vicarious Trauma
- DART Center for Journalism and Trauma
BACK TO TOP >
10 Killer Resources for New OSINT Analysts
Regardless of how much you might know, you can always benefit from the wisdom of others. And one way to learn from seasoned practitioners is to check out some of the books, blogs, and podcasts they’ve created about different topics in OSINT.
Whether laying out foundational principles or charting new terrain, the following resources are mind-expanding exercises in gathering intelligence. These should also be considered required reading for any new analysts looking to break into the field.

|
In Open Source Intelligence Techniques, author Mike Bazzell shares step-by-step his methods to locate information on targets through open sources. Chapters include uncovering hidden social media comments, finding content on the dark web, discovering website owner information through domain lookups, geolocating IP addresses, and extracting metadata from images. Perhaps more importantly, the book explores foundational concepts related to conducting investigations online, such as digital privacy and operational security. If you only buy one book on OSINT, be sure to get this one. |
|
|
Open Source Intelligence Methods and Tools: A Practical Guide to Online Intelligence represents an outstanding starting place for the beginner OSINT analyst. But you have lots of nuggets of wisdom in here for more experienced investigators too. In each chapter, authors Rami Hijazi and Nihad Hassan break down tools and tactics to collect information from public sources. Topics include gathering intel on competitors, predicting future industry trends, identifying organizational risks, navigating the dark web, and staying anonymous online. |
|
|
Cybersecurity expert Vinny Troia has earned a reputation as the go-to expert on digital forensics and breach remediation. His book, Hunting Cyber Criminals: A Hacker's Guide to Online Intelligence Gathering Tools and Techniques, breaks down how he uses OSINT to track criminals worldwide. And in each chapter, he shares with readers his process and tradecraft. Troia’s book is the closest thing you can get to looking over the shoulder of a world-class investigator. And his mix of story-telling, real-world examples, and hands-on tutorials makes for a gripping read. |
|
|
Mike Bazzell shares so much of his expertise with the OSINT community, we have included his resources on our list twice. Hiding from the Internet: Eliminating Personal Online Information is a master class in operational security. And in this book, Bazzell exposes how websites and applications leak our personal information to others. He also examines each source, revealing ways to shield your data from unwanted third parties. Whether you want to protect a client from a violent stalker or just safeguard your data from nosy marketers, this book is a must-read for anyone that values their privacy. And it is a fantastic resource for any security professionals involved in close protection. |

|
In war, parties on both sides flood the media with disinformation. So how do outsiders separate fact from fiction? Enter Bellingcat. Launched in 2014, Bellingcat has established itself as one of the most respected groups of investigative journalists worldwide. The agency has made a name for itself by exploiting open source intelligence to uncover everything from the perpetrators behind the downing of Malaysia Airlines Flight 17, suppliers of illegal weapons in the Syrian civil war, the assassins behind the poisoning of famed activist Alexei Navalny, and more. In addition to the group’s outstanding investigative work, Bellingcat also provides educational resources for OSINT analysts. |
 |
Do you need a way to stay up to date on the latest OSINT news? Then you will want to check out Secjuice. Written by a wide assortment of industry experts, the site provides coverage of recent events impacting the open source intelligence community. Popular topics include cybersecurity, hacking, OSINT tools, intelligence tradecraft, and network security. |

|
The OSINT Curious Project has emerged as the go-to learning resource for new and experienced analysts. Run by a group of volunteers, this non-profit organization provides news, how-to articles, and instructional videos to help readers explore their OSINT passions. And in addition to the website resources, the project organizers have also launched a regular podcast interview series featuring experts from across the field. |

|
Since OSINT is our bread and butter, we hope you don’t mind us adding our own Talking Threat Intelligence podcast to the list. Every other week, we invite a new guest to discuss issues and trends from the front lines of corporate security. And as you’d expect, open source intelligence represents a common theme on the show. Recent episodes include using OSINT for executive protection, how to debunk online misinformation, and the OSINT skills employers want right now. |
 |
The Layer 8 Conference is the first industry event dedicated solely to social engineering and intelligence gathering. In addition to the annual conference, organizers have also launched a podcast. In each episode, guests share tips, tricks, and stories from their work. Recent episode topics include using dating apps from an OSINT perspective, exploiting bias in social engineering, and the military’s human lie detector. |

|
If you work in the private sector, then you should check out The Business of Intelligence Podcast. In each episode, hosts Ryan Long and Michael Mallard discuss how intelligence can better serve corporate decision-makers. They break down what is and what’s not working in the industry, as well as how ambitious analysts can advance in their careers. Recent topics include improving relationships with clients, how to grow a corporate intelligence program, advice on building better relationships with decision-makers, and protecting your organization from disinformation. |
If you want to develop your tradecraft, then there’s no better way than getting your hands dirty by doing work in the field. That said, grounding yourself with a theoretical foundation will make you a better practitioner. Not to mention it will also dramatically shorten your learning journey.
The list of OSINT books, blogs, and podcasts above should provide more than enough material to get started.
Read more:
- 7 OSINT Books Every Analyst Should Read
- 7 OSINT Podcasts Every Analyst Should Follow
- 7 OSINT Blogs Every Analyst Should Read
BACK TO TOP >
5 Tips for Getting Started with OSINT
Breaking into open source intelligence can seem daunting – especially if you’re new to the field.
More established professions, like accounting or medicine, have well-established pathways for learning the trade. Not so with OSINT.
Because the field is so new, rookie investigators have few guideposts for direction. That can make it hard to know exactly where to get started.
That said, there are some concrete steps you can take right now to develop your skills as a researcher. So here are five things to consider doing next:
- Make a list of your skills and interests. Take some time to consider what you’re interested in and what skills you might already have. Can you speak another language? Do you have expert knowledge of military hardware? Are you fascinated with maps and geography? Do you have a programming background? Asking these questions will give you an idea of what type of OSINT research might interest you.
- Join your peers online. Twitter is the “water cooler” of the OSINT community. You can also find vibrant OSINT discussion forums on Discord and Reddit. If you don’t want to, you don’t need to participate in these conversations. You don’t even need to reveal your real identity. But these groups serve as the main place to debate and disseminate research. And having an account will allow you to follow other analysts, learn from their work, and ask questions.
- Follow experts. Once you join one of the big social networks, you’ll want to start following other OSINT researchers. That will allow you to learn about the tools, methods, and practices top analysts employ as part of their tradecraft. And as you spend more time following experts in the community, you will start to get a sense of which organizations focus on which topics.
- OSINT yourself. Test out your OSINT skills by searching your own digital footprint. Start by using Google and other tools to search for your information (i.e. usernames, phone numbers, email addresses, etc.) and build a profile. That should be a simple project as you can easily verify any details. You might also be surprised how much personal information you have exposed online.
- Practice, practice, practice. Once you have a few practice investigations under your belt, you will want to sharpen your OSINT skills further. Develop your geolocation abilities with GeoGuesser. Network with other analysts by joining a Trace Labs Capture the Flag event. Conduct mock investigations on a celebrity or organization you admire. All of these activities will make you a better researcher.
|
OSINT for Beginners Tip: Firstly, marketing tools focus almost exclusively on the biggest platforms. As a result, security teams could overlook threats lurking in smaller, more obscure online communities. Secondly, software tools built for marketers usually pull in data only once every few hours. That can cost organizations precious time when responding to a crisis. |
Read more:
BACK TO TOP >
10 OSINT Terms You Need to Know
- Social Media Intelligence (SOCMINT): A sub-discipline of OSINT which refers to the collection and analysis of information from social media platforms.
- Operational Security (OPSEC): Processes used to deny a potential adversary any type of intelligence that could jeopardize the confidentiality or security of the mission.
- Imagery Intelligence (IMINT): The tools, techniques, and technologies that allow for the analysis of information from imagery.
- Human Intelligence (HUMINT): Any intelligence derived from information captured from human sources, as opposed to more technical methods like imagery or signals intelligence.
- Social Engineering: The use of deception to manipulate a person into performing an activity that may not be in their best interest, such as divulging confidential information or granting access to a secure facility.
- Raw Data: Any facts or statistics that remain unaltered from their original sources, such as EXIF data, website comments, network traffic logs, or social media posts.
- Finished Intelligence: Raw data that has been processed to gain context and become actionable, also referred to as ‘cooked data.’
- Google Dorking: The use of advanced search operators to find information that is not readily accessible through simple Google searches.
- Open Source: Any information available for consumption by the general public and widely accessible.
- Threat Intelligence: Actionable information collected from different sources about current or potential risks against an organization.
|
OSINT for Beginners Tip: |
OSINT for Beginners: The Bottom Line
After diving into your own OSINT research, you might soon find yourself in over your head. You may see expert researchers discussing concepts and techniques you don't understand. Or geolocation challenges that look so simple in YouTube videos now seem impossible to complete yourself.
Don’t give up! OSINT tradecraft takes time to develop and master. Every researcher you admire today once started as a beginner. But as long as you have fun and keep practicing, you will get better over time.
Good luck!
BACK TO TOP >





